Short Posts
A curated collection of brief posts that highlight the key ideas, trends, and tips you need to know.
04 Mar 2025
Lowering MTTD & MTTC: The Power of Integrating SIEM with UBA for Cybersecurity?
Cyberattacks are a growing menace—with a new hacking attempt launched every 39 seconds, 6.3 trillion intrusion attempts, and 5.5 billion malware attacks occurring in 2022 alone. In such a grave climate, organizations must be equipped to detect, prioritize, and respond to threats quickly. In fact, while the mean time to detect (MTTD) a breach was 207 days and the mean time to contain (MTTC) was 70 days in 2022, integrating a SIEM solution with user and entity behavior analytics (UBA) can dramatically bring those numbers down.
Given the sheer volume and sophistication of these threats, anomaly detection and fraud prevention have become well-known and essential approaches to identifying malicious activity in real-time. Here's how cutting-edge UBA transforms user behavior into a fraud-fighting superpower—and some real-world examples from our work at CrossClassify:
Anomaly Detection
- Advanced ML algorithms, statistical models, and heuristics enable UBA to catch subtle deviations while continuously updating a dynamic risk score.
- Key features include sudden location changes, typing speed variations, unusual page navigation patterns, and inconsistent time zone usage, with real-time alerts triggered when risk thresholds are breached.
- Fine-tuned thresholds ensure only truly risky behavior is flagged, helping reduce false positives.
- Our team at CrossClassify has leveraged these features to detect fraud in Account Takeover (ATO) and Account Opening (AO) domains:
ATO fraud: When attackers use stolen credentials to access existing accounts.
AO fraud: When fraudulent new accounts are created using fake or stolen identities.
These insights are critical not only for preventing ATO and AO but can also extend to blocking transactional data fraud.
Our Experience at CrossClassify
At CrossClassify, our team has successfully applied UBA to combat fraud in areas like account takeover and fraudulent account opening services. By analyzing behavioral cues such as location shifts, typing speeds, page navigation, and time zone variations, we’ve achieved actionable insights that significantly reduce fraud risks. These techniques also help prevent transactional data fraud, safeguarding your organization against a wide spectrum of financial crimes.
More Info:
https://lnkd.in/epb6ZQ-n
https://lnkd.in/eBycWsjb
https://lnkd.in/eBycWsjb
https://lnkd.in/eyArRXRx
https://lnkd.in/eNxFjtzH
https://lnkd.in/eNxFjtzH

04 Mar 2025
How 700 Million EA Accounts Were Compromised: A Wake-Up Call for Cybersecurity!
I recently read an eye-opening article by Battleda that dissects a real-world EA account takeover incident. The detailed analysis not only highlights the vulnerability but also walks through the attacker’s step-by-step approach, offering invaluable insights for cybersecurity professionals.
What Happened?
The attacker exploited weaknesses in EA’s authentication and account management systems. Here’s a brief overview of the attack vector:
- Initial Access: Targeted exposed endpoints and exploited a lack of robust input validation to launch a series of account takeover attempts.
- Exploitation Technique: Leveraged weak security measures—such as insufficient rate limiting and potential credential reuse—to bypass traditional safeguards.
- Escalation: Took advantage of session management vulnerabilities to escalate access, eventually compromising user accounts and personal data.
Key Lessons and Takeaways:
- Vulnerability Identification: Pinpointing specific flaws is essential for implementing effective countermeasures.
- Defense in Depth: Relying solely on a single security layer is risky. A multi-layered approach, including robust authentication mechanisms and continuous monitoring, is crucial.
- Proactive Security Measures: Regular security assessments, timely updates, and comprehensive employee training are vital in preventing similar breaches.
This case study serves as a stark reminder of the importance of rigorous security and account protection measures. As cyber threats evolve, organizations must continuously evaluate and enhance their security posture to safeguard both their assets and their users' data.
Dive into the full article for technical details and mitigation strategies: [EA Account Takeover] (https://lnkd.in/eNf_BkFd)
Fraud Detection Spotlight:
For those looking to bolster their defenses, consider exploring **CrossClassify**—a trusted fraud detection service offering solutions in Account Takeover (ATO) and Account Origination (AO) protection. Their innovative approach helps organizations proactively detect and prevent fraud before it happens.
How is your organization preparing to tackle similar threats? Let’s share insights and discuss best practices for a safer digital future!

24 Feb 2025
Why Smart Companies Are Betting Big on UBA for Growth & Security
What’s the most common question I get after explaining the basics of UBA?
“Okay, how do we apply it in the real world—beyond just cybersecurity? And where?”
UBA in Marketing
Personalization isn’t just a buzzword. It’s about understanding every click, scroll, and interaction users make.
Recommendation Systems: UBA helps model user behavior—think mouse clicks, page views, and timing—to predict what they’ll want next. This is the core of modern Information Retrieval (IR). It’s more than “here’s a product you might like”—it’s about predicting intent and delivering the right offer at the right time.
Heatmaps & Session Recordings: Visualize exactly where users engage most on your site. This feature is key for refining marketing strategies and boosting conversion rates.
UBA in UX
UX designers are obsessed with how people move through a site or app—and UBA turns that obsession into data-driven insights.
Mouse Movement Tracking: It’s not just about “where do they click?” but also tracking mouse movements, dwell time, and content skimming. These subtle signals reveal frustrations, highlight what’s working, and spark ideas for better navigation. Data replaces guesswork.
Scroll Depth Analysis: Understand how far users scroll on your pages. This insight is invaluable for tweaking content layout and enhancing overall user experience.
UBA in Fraud Prevention
Online fraud has gotten sneaky. But so has UBA.
Invisible Signals: It picks up on hesitation time on forms, typing speed, and abnormal page navigation. For example, if a user typically types at 60 WPM but suddenly slows down from a different IP, UBA flags it. This proactive defense means no more waiting for a 2 a.m. bank call.
Device Fingerprinting & Geolocation: Beyond the basics, tracking device signatures and location anomalies can catch account takeover attempts early.
Our Experience: At CrossClassify, we’ve used several UBA features for fraud detection in Account Takeover and Account Opening. Based on our experience, we’ve found that some of these user behavior features are game-changers for flagging suspicious account actions. What About Other Industries?
E Commerce and banking are just the beginning. UBA’s influence is spreading
E-Learning: Adapting to student interaction styles.
Healthcare: Tracking patient engagement.
The possibilities are massive.
Ready to see how UBA can level up your strategy?
Check out these must-reads:
5 Behavior Analytics Use Cases + Examples That Work (https://lnkd.in/eeiJfNBq)
The Top 17 UEBA Use Cases to Protect Your Business (https://lnkd.in/ez26Vgjg)
What’s been your biggest “aha” moment using UBA? Let’s discuss!

18 Feb 2025
UBA: The Secret Weapon in Modern Cyber Defense
Did you know that traditional rule-based security systems are becoming obsolete? In a world of increasingly sophisticated cyber threats, you need something smarter. Enter User Behavior Analytics (UBA)—think of it as the AI-powered detective watching your network, learning what’s “normal,” and flagging suspicious activity before it becomes a full-blown crisis. So, what is UBA?
UBA isn’t just about detecting breaches after they happen; it's about predicting them. It analyzes data from log files, network traffic, and access patterns to establish a baseline for normal behavior. When something unusual happens—like a login from a new location or access to sensitive files out of nowhere—UBA detects the anomaly and alerts your security team. This is how you spot insider threats, compromised credentials, and advanced persistent attacks before they escalate. And then, there's UEBA...
UBA focuses on human behavior, but what about devices, apps, and servers? That's where User and Entity Behavior Analytics (UEBA) comes in. UEBA gives you a broader view of potential threats, catching multi-faceted attacks that might slip through the cracks of traditional tools.
Key Benefits of UBA/UEBA: Real-Time Monitoring: Keep your network under constant surveillance. Advanced Analytics: AI and machine learning adapt to new threats in real time.
Risk Scoring & Anomaly Detection: Minimizing false positives while highlighting true threats.
Enhanced Visibility: Unlike traditional SIEM tools, UBA/UEBA tells you who is behind suspicious activity.
Faster Threat Detection: Immediate alerts mean you’re not playing catch-up. Better Compliance, Lower Costs: Detailed logs help meet regulations and streamline operations.
Proactive Security: Stop breaches before they happen, not after. As we kick off this series, I’ll dive deeper into how UBA/UEBA is transforming cybersecurity and what it means for your organization’s defense strategy.
What security challenges are you facing? Let’s discuss in the comments!
For more insights, check out:
IBM's Take on UBA (https://lnkd.in/eJCnrX43)
SentinelOne's Overview of UEBA (https://lnkd.in/e2Y2w-6Z)

13 Feb 2025
Redefine Identity Protection in Cybersecurity
Protecting digital identities with advanced AI and behavioral analysis.
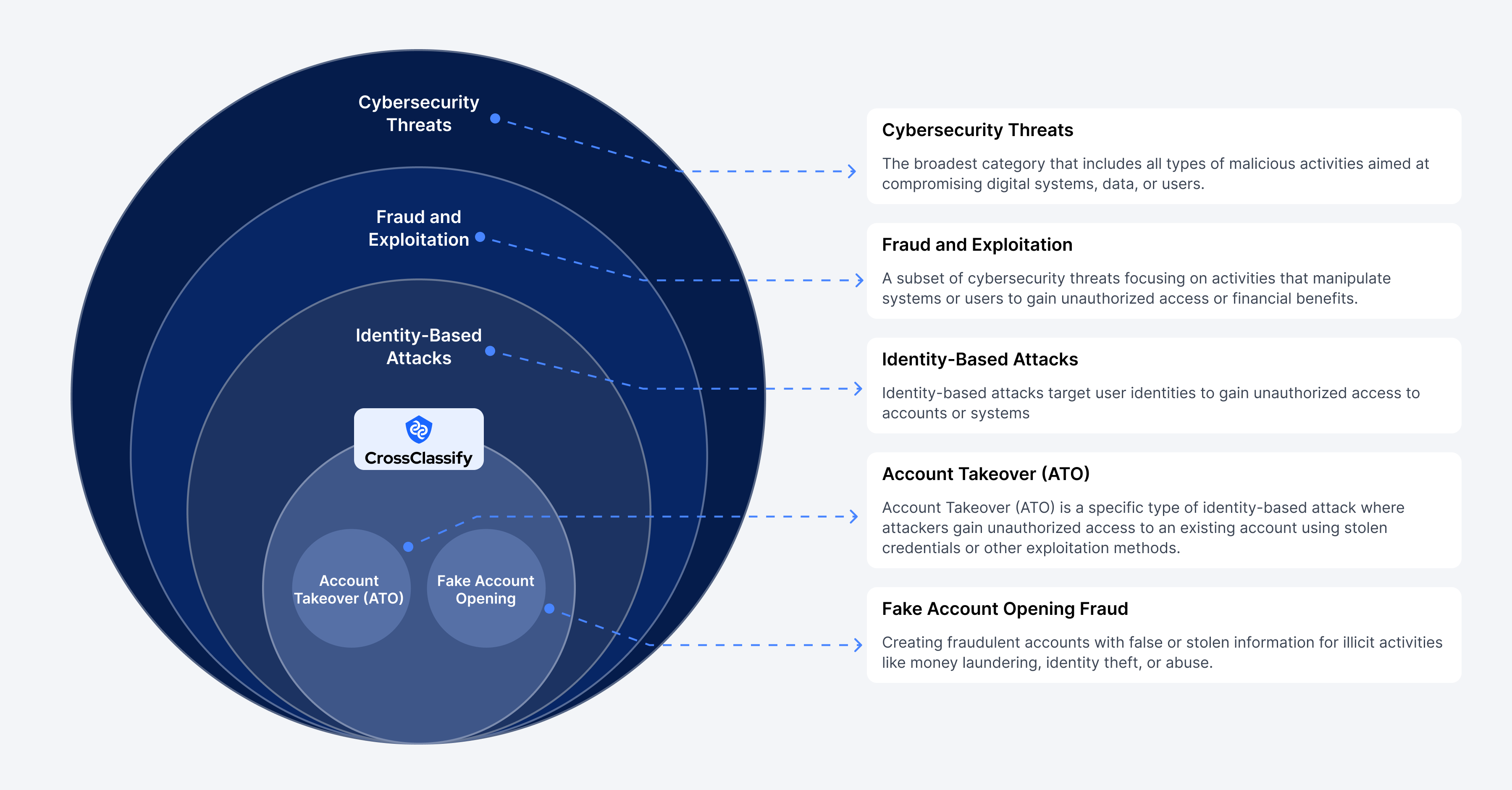
Preventing account takeovers and identity fraud before they happen. Cybersecurity is a multi-layered battlefield, where threats evolve and adapt at an alarming rate. From nation-state attacks to financial fraud, businesses today face an ever-growing range of risks. At the highest level, cybersecurity threats encompass everything from malware and ransomware to phishing and social engineering. As attackers refine their tactics, organizations must implement proactive security measures to mitigate risks before they escalate into breaches. One critical subset of cybersecurity is Fraud and Exploitation, which targets weaknesses in applications, APIs, and authentication systems. Web and mobile applications, often the primary access points for users, are highly vulnerable to exploits such as credential stuffing, session hijacking, and man-in-the-middle attacks. These vulnerabilities allow attackers to manipulate systems, steal data, or gain unauthorized access, leading to financial losses and reputational damage for businesses.
Within fraud and exploitation lies Identity-Based Attacks, a domain where CrossClassify (CC) operates as a leader in protection. Identity threats, such as Account Takeover (ATO) and Fake Account Opening (AO), are two of the most prevalent and damaging forms of fraud today. Attackers compromise legitimate accounts or create synthetic identities to exploit systems, bypassing traditional security measures. CrossClassify leverages AI-powered behavioral analysis and device fingerprinting to detect and block these threats in real-time, ensuring businesses stay ahead of identity fraud. In a world where digital identities are constantly under attack, proactive defense is no longer optional—it's a necessity.
11 Feb 2025
The Shift to Digital Prescriptions: Are We Secure?
As we discussed in the last post, the pandemic significantly accelerated the adoption of digital technologies in healthcare. Among these, digital prescriptions stand out as one of the most important and rapidly growing innovations in the post-COVID-19 era.
The pandemic revolutionized healthcare, pushing handwritten prescriptions aside for digital ones. But with this innovation comes new challenges—particularly in data security.
Did You Know?
30% of global data now comes from healthcare. (IDC (https://lnkd.in/eQuq5s4U))
Healthcare breaches reached record levels in 2023, with over 1,100 incidents in the U.S. alone.
(Statista (https://lnkd.in/eQuq5s4U))
The average cost of a breach hit $11M in 2023, up 53% in just three years. (Healthcare Dive (https://lnkd.in/eQuq5s4U))
Digital prescriptions store sensitive data, making them prime targets for cyberattacks. Threats like credential theft, fraudulent prescriptions, and data tampering are real risks.
How can we secure this transformation?
Implement multi-factor authentication.
Use end-to-end encryption.
Deploy real-time monitoring systems.
As healthcare continues to innovate, we must build trust by safeguarding patient data. Let’s not compromise security for convenience.
What security measures do you think are essential for digital healthcare? Share your thoughts below!

27 Jan 2025
Paper-Free Medicine: Transforming Care While Safeguarding Data
We live in a time where the physical world is diving headfirst into the digital realm. From digital prescriptions to online doctor appointments and even virtual therapy, technology is revolutionizing healthcare. The convenience is undeniable—but it comes with significant cybersecurity risks.
The Fast-Forward Button:
The pandemic accelerated this transformation, pushing healthcare to go paperless almost overnight. While this rapid shift improved access and efficiency, it also raised a critical question:
Did we lay the cybersecurity foundation necessary to protect sensitive patient data?
The Reality Check:
Over 93% of healthcare organizations have experienced a data breach in the last three years. (Source: Ponemon Institute (https://www.ponemon.org/))
The healthcare industry accounted for 20% of all reported data breaches in 2022, making it one of the most targeted sectors.
The move to digital means data is more exposed to threats like:
Account Takeovers (ATO): Cybercriminals can exploit stolen credentials to access patient portals and sensitive health records.
Session Hijacking: Unprotected sessions leave the door open for unauthorized access and manipulation.
What Does This Mean for Healthcare?
Paper-free medicine isn’t just about convenience—it’s a call to action for more advanced cybersecurity measures.
Encryption, multi-factor authentication (MFA), and real-time monitoring must become standard in safeguarding patient data.
As we embrace paperless healthcare, we must ask ourselves:
Are we ready to protect the data entrusted to us?
The digital transformation in healthcare is a leap forward, but it demands an equal leap in cybersecurity. Let's build a safer digital healthcare system together.
What measures do you think are essential to secure paperless healthcare? Share your thoughts!

27 Jan 2025
Protecting Insurance Customers from the Growing Threat of Account Takeover
The insurance sector has made huge strides in digital innovation—unfortunately, so have cybercriminals. Account takeover (ATO) remains one of the most alarming methods fraudsters use to exploit policyholder data and company resources. Once criminals gain unauthorized access to an account, they can:
Submit fraudulent claims: For example, a fraudster could access a life insurance policyholder's account and file a claim for a non-existent death, rerouting the payout to their own account.
Alter sensitive customer information: Fraudsters might change contact details, such as email or phone numbers, to intercept communication from the insurer, leaving the real policyholder unaware.
Steal personal and financial data: Criminals can extract Social Security numbers, bank account details, or medical records to sell on the dark web or use for identity theft. Damage brand reputation and erode trust: A single high-profile breach could tarnish an insurer's reputation, causing customers to lose confidence in the company's ability to protect their sensitive information.
The Numbers Don’t Lie According to recent industry analyses, over 60% of insurance companies worldwide have experienced an increase in ATO attempts over the last year. The cost of these attacks goes beyond immediate financial losses—there’s also the long-term impact on customer trust and regulatory compliance.
What Can We Do?
1. Leverage Advanced Analytics & AI to spot unusual login or claim behavior in real-time.
2. Deploy Multi-Factor Authentication and context-based access controls to verify users.
3. Educate Policyholders on recognizing phishing attempts and protecting their credentials.
By proactively addressing ATO risks, insurers can protect their bottom line, stay ahead of evolving cyber threats, and safeguard the trust policyholders place in them.
How is your organization defending against account takeover schemes? Feel free to share your insights or questions below.
Anxiety, guilt, and stress are common psychological consequences, disrupting victims’ daily lives and compounding their recovery
Beyond individual harm, businesses suffer from damaged reputations, strained customer relationships, and loss of loyalty
Financial institutions play a critical role in aiding recovery. Quick action to secure accounts, empathetic communication, and enhanced security measures can ease the process. But rebuilding trust takes longer—often far longer than restoring the stolen funds.
Recovering from account takeover is a journey that goes beyond reimbursing financial losses. It requires addressing emotional impacts and mending fractured relationships. Financial recovery is achievable, but trust recovery demands time, effort, and unwavering commitment.
Let’s recognize and address the true cost of fraud—not just in dollars but in trust. How do you think organizations can better support victims?

09 Jan 2025
How Scammers Exploit Vulnerable Patients Through Healthcare Apps
As healthcare app owners, you interact with people during their most vulnerable moments—managing illnesses, medications, and financial stress. Unfortunately, this makes patients prime targets for scammers.
The Growing Threat of Healthcare Scams:
In 2024, 677 healthcare data breaches affected 182.4 million individuals, highlighting the alarming scale of attacks. Fraudsters exploit patients’ fears and needs, often pretending to be trusted entities to steal data, money, or access to services.
The Limits of User Education
User education is valuable but not enough in healthcare:
1. Patients under stress may miss scams.
2. Scammers exploit emotional vulnerability.
3. Elderly or less tech-savvy users struggle with cybersecurity training.
A Smarter Approach: Proactive Security for Healthcare Apps
To truly safeguard healthcare apps, healthcare app owners must prioritize proactive solutions that go beyond user education:
1. Continuous Monitoring: Real-time threat detection and blocking.
2. User Behavior Analysis: Spotting abnormal patterns to detect fraud.
3. Link Analysis: Uncovering hidden connections to prevent scams.
Healthcare apps are more than just platforms—they’re critical lifelines. For healthcare app owners, protecting users means not only preventing scams but also maintaining their trust during some of the most challenging moments of their lives. By prioritizing proactive security, we can create safer, more secure apps that empower patients and protect their sensitive information.
Let’s work together to build a safer healthcare ecosystem for everyone.

07 Jan 2025
When Patient Data Breaches Turn Deadly: The True Cost of Exposure
In 2024 alone, over 100 million patients’ data was exposed in a single breach involving UnitedHealth's technology unit, marking one of the most devastating healthcare data compromises in history (source). When patient data is disclosed in a breach, the consequences extend far beyond financial loss or identity theft. For patients, it can disrupt lives, compromise safety, and erode trust in the healthcare system.
How Patient Data Breaches Directly Impact Individuals Delayed or Incorrect Care leading to death: If healthcare systems are compromised, tampered records or inaccessible data during emergencies can lead to delayed or incorrect diagnoses and treatments—potentially putting lives at risk.
Medical Fraud: Stolen medical records can be used to falsify insurance claims, obtain unauthorized treatments, or purchase prescription drugs under a patient’s name, leaving them with financial and legal complications.
Privacy Violations: The exposure of sensitive health details, such as diagnoses or treatments, can cause emotional distress, stigma, or embarrassment for patients.
Identity Theft: Leaked personally identifiable information (PII), such as Social Security numbers and contact details, can be exploited for identity theft, leading to fraudulent financial activities.
Targeted Scams: Cybercriminals often use breached data to create highly convincing phishing attacks, specifically targeting patients with fake medical bills or insurance-related scams.
Loss of Trust: Patients may lose confidence in the healthcare provider or system, fearing that their private information is no longer secure. This erosion of trust can discourage individuals from seeking necessary medical care.
Why It Matters Patient data disclosure isn’t just about numbers; it’s about real people whose safety, privacy, and well-being are at stake. When a healthcare data breach occurs, the ripple effects can follow a patient for years, making robust cybersecurity and data protection practices a moral imperative.

30 Dec 2024
Cybersecurity Threats in Healthcare: A Growing Concern to Lives
Healthcare is more than a service—it's a lifeline. Yet, the sensitive data that powers this industry is under constant threat. A healthcare data breach doesn’t just compromise privacy; it puts lives at risk.
What Makes Healthcare Data So Critical?
Healthcare data encompasses some of the most sensitive information, including:
Protected Health Information (PHI): Medical records, diagnosis details, and treatment plans.
Personally Identifiable Information (PII): Social Security numbers, contact information, and birthdates.
Financial Information: Credit card numbers, banking details, and billing data.
Health Insurance Data: Insurance IDs, claims, and payment records.
Hackers target this data not just for financial fraud but to sell it on the dark web or even disrupt patient care systems.
The Alarming Scale of Breaches in 2024 According to HIPAA Journal, 13.5 million patients’ information has been disclosed in 2024 alone. Personal health information is worth at least 10 times more than financial information on the black market (source). This makes healthcare data breaches significantly more damaging, as attackers prioritize such data for its enduring value and diverse exploitation opportunities. Unlike financial information, healthcare data can’t be reset, canceled, or replaced—it follows the patient for life, making the consequences far-reaching and severe.
When Healthcare Data Breaches Risk Lives in a Complex System The variety of actors in healthcare—hospitals, clinics, insurers, pharmacies, labs, and even tech providers—creates a complex web of access points. A single vulnerability in this chain can lead to catastrophic breaches. But the stakes go beyond financial and reputational loss. In extreme cases, breaches can delay critical care, tamper with patient records, or lead to life-threatening outcomes. When a patient's safety is on the line, cybersecurity becomes non-negotiable.
In future posts, we’ll dive into how specific actors—hospitals, insurers, and tech providers—can combat these threats effectively. Remember that when a patient's safety is on the line, cybersecurity isn’t just a technical issue—it’s a moral and life-or-death imperative. And it’s very important to prevent it before happens.
23 Dec 2024
ATO fraud costs you money and trust, one recovers fast, the other scars forever
Account takeover (ATO) fraud doesn't just result in financial losses—it shakes the very foundation of trust between customers and institutions. While stolen funds can be restored after weeks or months of effort, the erosion of trust leaves a deeper, lasting scar.
Victims of fraud often report feelings of betrayal and powerlessness. Studies show:
45% of fraud victims stop using the affected financial institution entirely, while 17% close their accounts
Anxiety, guilt, and stress are common psychological consequences, disrupting victims’ daily lives and compounding their recovery
Beyond individual harm, businesses suffer from damaged reputations, strained customer relationships, and loss of loyalty
Financial institutions play a critical role in aiding recovery. Quick action to secure accounts, empathetic communication, and enhanced security measures can ease the process. But rebuilding trust takes longer—often far longer than restoring the stolen funds.
Recovering from account takeover is a journey that goes beyond reimbursing financial losses. It requires addressing emotional impacts and mending fractured relationships. Financial recovery is achievable, but trust recovery demands time, effort, and unwavering commitment.
Let’s recognize and address the true cost of fraud—not just in dollars but in trust. How do you think organizations can better support victims?

24 Dec 2024
Are We Still Talking About the Same Type of Fraud?
In cybersecurity, consistent terminology is essential for tackling threats like account takeover (ATO) fraud. Imagine a team investigating a breach: one member calls it "credential stuffing," another says "identity theft," while someone else refers to "session hijacking".
Though they're addressing the same issue, the varied terminology can cause confusion and delay. The Difficulty with Divergent Terminology, different names for the same fraud disrupt coherence, delay responses, and create challenges in aligning strategies. Why Consistent Terminology Matters:
Clarity: Ensures all stakeholders are on the same page. Efficiency: Speeds up communication and decision-making. Effectiveness: Strengthens collaborative defenses.
Key Synonyms Explained:
Account Takeover (ATO): Unauthorized access to a user’s account to steal information or commit fraud.
Credential Stuffing: Using stolen login credentials from one breach to access accounts on other platforms.
Identity Theft: Stealing personal information to impersonate someone for fraudulent purposes.
Session Hijacking: Exploiting a valid session to gain unauthorized access to data or services.
Unauthorized Access: Illegally entering systems or accounts, often leading to data breaches.
Phishing: Tricking users into sharing sensitive information by posing as a trusted entity.
Brute Force Attack: Guessing passwords systematically to break into accounts.
Man-in-the-Middle Attack: Intercepting communication between parties to access data.
Social Engineering: Manipulating individuals to reveal confidential information.
Malware Injection: Deploying malicious software to compromise account security.
Standardizing how we talk about these threats enhances our ability to combat them effectively. A shared language strengthens our defenses and helps protect what matters most.

17 Dec 2024
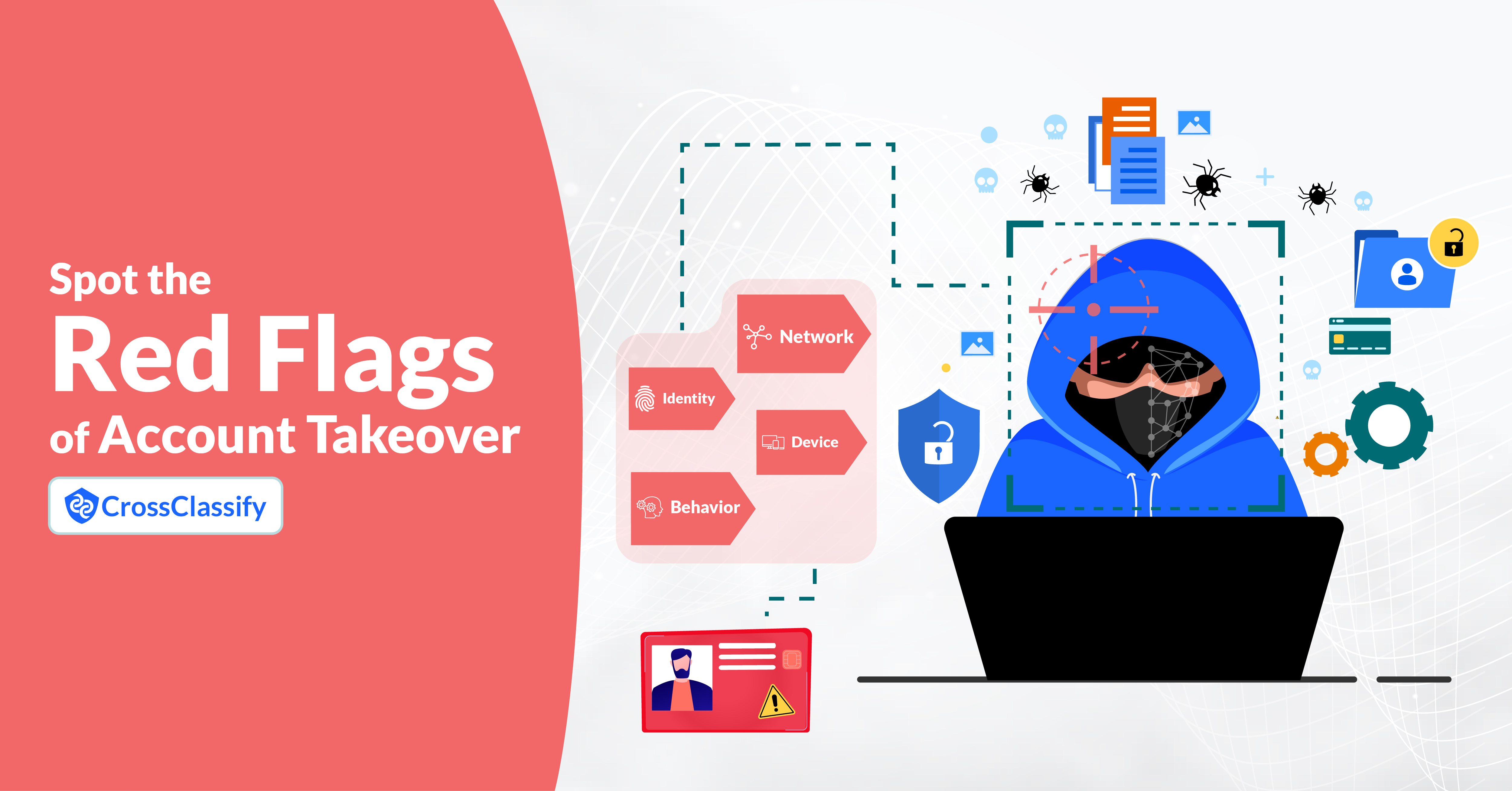
Protect Your Accounts: Spot the Red Flags of Account Takeover
Account takeovers (ATO) (https://lnkd.in/e4ryptur) can strike without warning, causing financial loss, reputational harm, and a lot of stress. But by staying vigilant, you can catch the warning signs early and take action to secure your accounts.
Here are 4 key red flags to watch for:
Unusual Login Patterns Frequent logins from unfamiliar devices, locations, or time zones? Or suddenly logged out of your account? These are clear signs of suspicious activity.
Suspicious Changes in Account Details Unexpected updates to your email, phone number, or security settings could mean an attacker is locking you out.
Sudden Spike in Account Activity Large transactions, bulk messages, or changes to stored data? Attackers often exploit compromised accounts fast and hard.
Login Notifications from Unrecognized Devices/Locations Alerts about login attempts from unknown places? Even failed attempts indicate your account might be a target.
Pro Tip: Strengthen your defenses with multi-factor authentication (MFA) and behavioral analytics. Prevention is your best weapon!
Are you or your business doing enough to safeguard your accounts? Let's discuss strategies in the comments!
17 Dec 2024
Account Takeover (ATO): A Growing Threat We Can't Ignore
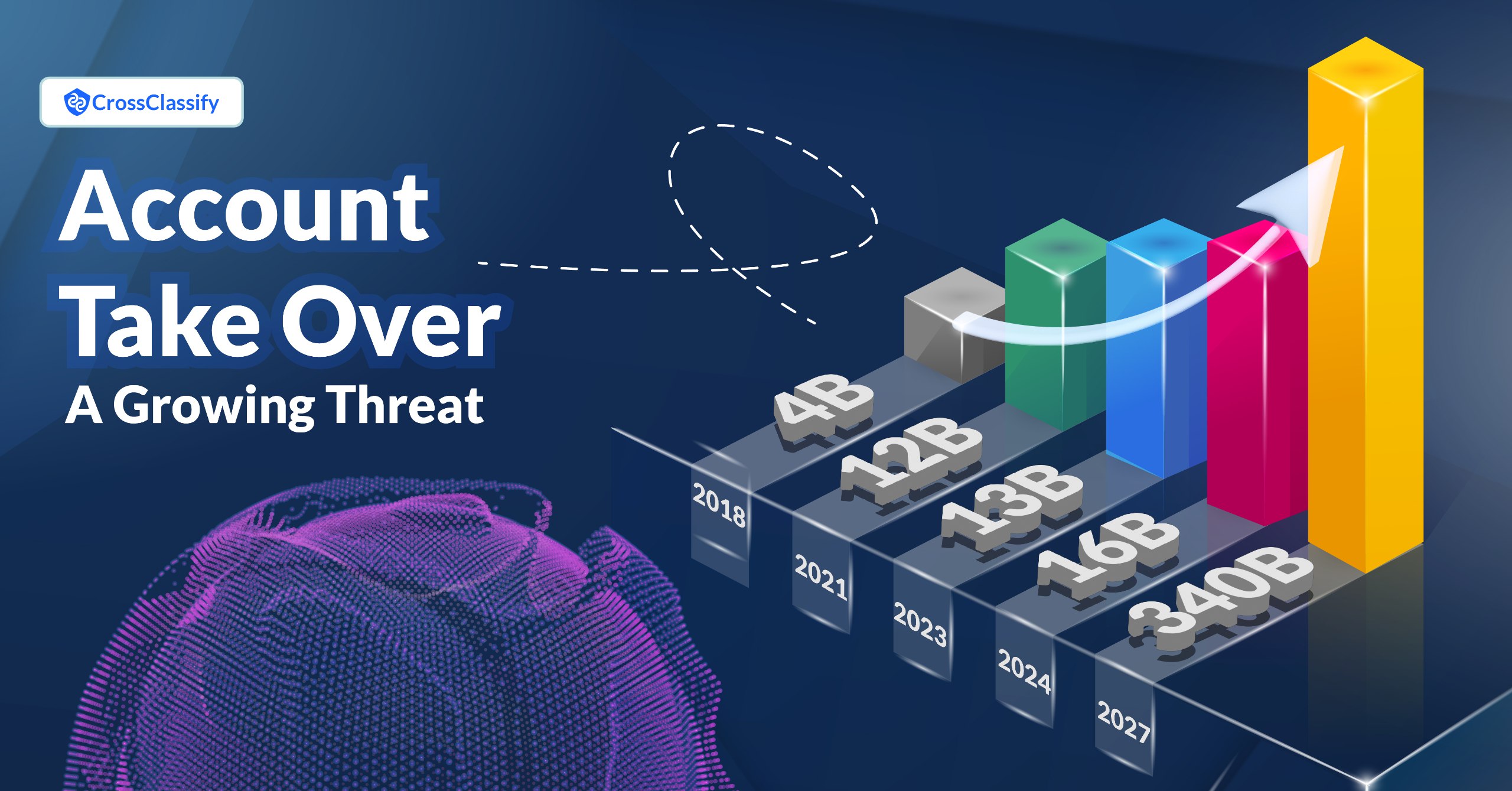
In 2024, 24% of global consumers were victims of ATO—up from 18% last year.
But why are we saying that ATO is a growing threat? Let's take a look at ATO losses in recent years:
2018: Losses totaled $4 billion.
2021: Surged to $12 billion—a 3x increase from 2018.
2022: Estimated global losses were $11.4 billion.
2023: Climbed to nearly $13 billion.
2024: With a 24% increase in attacks, projected losses could reach $16 billion.
Reports suggest global ATO fraud losses may exceed $343 billion by 2027!!!! The question is: Are we prepared to fight back? Let’s review the ATO definition first:
ATO happens when attackers gain unauthorized access to legitimate accounts using stolen credentials or social engineering. Once inside, they can steal personal data, drain finances, and damage customer trust. For businesses, this means lost revenue, reputation damage, and costly recovery efforts. Industries like e-commerce and finance are especially at risk, facing millions in potential losses. As ATO attacks grow, building stronger defenses is more critical than ever. Despite advancements in AI, ATO remains a major threat, particularly to industries like e-commerce and finance. In the coming weeks, I'll dive deeper into questions like: What will ATO look like by 2027?
Why do we still face ATO with all the AI advancements that we had these recent years?
Are businesses the most vulnerable section of ATO fraud? Stay tuned for more insights on understanding and combating ATO.