Last Updated on 29 Oct 2024
The Growing Threat of Account Opening Fraud: Impacts, Detection, and Prevention
Share in

Key Notes:
The Growing Challenge of Account Opening Fraud
Account opening fraud has escalated significantly in recent years, posing substantial risks to both businesses and consumers. In 2023, fraudulent new account creations accounted for approximately 9% of all new accounts, highlighting the growing sophistication of fraudsters (SpyCloud). Also, 13.5% of digital bank accounts opened in 2023 were suspected to be fraudulent (Microblink).
Account opening fraud is a pressing issue across multiple domains, including financial services, e-commerce, healthcare, and telecommunications, each facing unique challenges and significant losses. In the financial sector, fraudulent account openings contribute to multi-billion-dollar annual losses, with reports indicating that synthetic identity fraud alone costs the industry upwards of $6 billion yearly. E-commerce platforms face substantial risks, as fraudsters exploit new account promotions and loyalty programs, feeding into a global digital fraud estimate of around $41 billion. Healthcare systems suffer from medical identity theft and resource siphoning, while the telecommunications industry battles scams facilitated by fake accounts. These alarming figures emphasize the urgent need for industries to adopt stronger identity verification and fraud prevention measures to mitigate these growing threats
This surge is largely attributed to advancements in identity theft and the use of fraudulent documentation. The repercussions are extensive: businesses face financial losses, reputational damage, and increased operational costs, while consumers suffer from compromised personal information and potential financial harm. Given the escalating nature of this threat, it is imperative for businesses to implement robust measures to detect and prevent fraudulent activities, thereby safeguarding their operations and protecting their customers.
Synonyms and Related Terms for Account Opening Fraud
Here are some alternative names and terms commonly used to refer to account opening fraud:

Uncovering the Why: Root Causes and Motivations Behind Account Opening Fraud
Uncovering the Why: Root Causes and Motivations Behind Account Opening Fraud
Account opening fraud is driven by various motivations, from financial gain to identity theft schemes. Key root causes include the exploitation of weak identity verification processes, advancements in synthetic identity creation, and the abundance of stolen personal data from breaches. Understanding these motivations helps businesses fortify their defenses and mitigate risk:
Root Causes of Account Opening Fraud:

Motivations Behind Account Opening Fraud:
Understanding Account Opening Fraud Tactics
Account opening fraud is a significant threat to financial institutions and consumers alike. Fraudsters employ various tactics to exploit vulnerabilities in the account creation process, aiming to gain unauthorized access to financial resources. By understanding these mechanisms, businesses can better protect themselves and their customers from fraudulent activities. Below are some common tactics used in account opening fraud:

1. Synthetic Identity Creation
Fraudsters blend real and fake information to create synthetic identities. They may use stolen Social Security numbers combined with fictitious names, addresses, and birthdates.
2. Use of Stolen Personal Information (Identity Theft)
Fraudsters use stolen personal data from data breaches, phishing attacks, or social engineering to impersonate real individuals and open accounts.
3. Automation and Bots
Sophisticated fraudsters use automation tools and bots to scale account creation, making it possible to open thousands of accounts quickly and efficiently.
4. Manipulation of Verification Processes
Fraudsters exploit weaknesses in identity verification systems, such as relying on easily manipulated documents or superficial ID checks.
5. Social Engineering and Phishing
Using deception to trick individuals or employees into sharing sensitive data that can be used for fraudulent account creation.
6. Exploitation of Weak KYC (Know Your Customer) Protocols
Fraudsters target institutions with minimal or outdated KYC procedures, where identity checks are not rigorous enough to detect fraudulent behavior.
7. Use of Proxy Servers and VPNs
Fraudsters use proxy servers and VPNs to conceal their IP addresses and locations, making it harder to detect suspicious behavior during account creation.
8. Financial Incentives and Exploiting Promotions
Some fraudsters specifically look for opportunities to open accounts to take advantage of welcome bonuses, cashback offers, or referral schemes.
Types of Account Opening Fraud
Account opening fraud comes in many forms, each posing distinct challenges to different industries. Understanding these variations is key to recognizing how fraudsters adapt their strategies to exploit vulnerabilities. This section will outline the main types of account opening fraud and their impacts, helping businesses and readers stay informed and prepared.
1. Synthetic Identity Fraud
2. Third-Party Fraud (Impersonation Fraud)
3. First-Party Fraud (Application Fraud)
4. Account Farming: Exploiting Free Trials and Bonuse Abuse
5. Money Mule Accounts

6. Synthetic Business Fraud
7. Loan Stacking
8. New Account Fraud for Fake Review Manipulation
9. Ban Evasion Through New Account Creation
Scam Strategies Driving Account Fraud
Scams play a pivotal role in facilitating account opening fraud by exploiting vulnerabilities and manipulating unsuspecting users or platforms. Fraudsters use various scam strategies, such as phishing and social engineering, to acquire the information or resources needed to create fraudulent accounts. These accounts are then used for further illicit activities, including identity theft, fake transactions, and financial scams. Understanding how scams contribute to account opening fraud is essential for businesses to strengthen their security measures and reduce risk:
1. Fake Accounts as Scam Tools
Fraudsters create fake accounts to impersonate legitimate users or businesses, which enables scams such as fake sales, fraudulent listings, or false reviews. These accounts build credibility for scams, making it easier to deceive unsuspecting victims.
2. Phishing for Account Setup
Scammers use phishing techniques to collect personal data from victims, which is then used to open fraudulent accounts in their names. This method allows fraudsters to bypass traditional identity verification checks and commit financial fraud.
3. Money Mules and Scam Proceeds
Fraudulent accounts are often used to recruit “money mules†or to launder money obtained from scams. This practice complicates tracking the source of illegal funds, making scams harder for authorities to trace and disrupt.
4. Amplifying Scams on Digital Platforms
Multiple fake accounts allow fraudsters to execute scams at scale across social media, e-commerce sites, and other digital platforms. This enables them to spread misinformation, conduct fraudulent transactions, and manipulate public perception.
5. Romance Scams and Fake Profiles
Fraudsters create fake accounts on dating and social platforms to establish trust with victims. They exploit this trust to manipulate and solicit money under false pretenses, using emotional leverage to defraud their targets.
Key Indicators of Account Opening Fraud
Detecting account opening fraud early is crucial for preventing financial losses and protecting consumers. Key indicators can help businesses identify fraudulent activity during the account creation process, allowing for timely intervention and stronger fraud prevention.
1. Unusual or Inconsistent Data
Data provided during account opening that doesn’t align with typical patterns, such as mismatched names and addresses or invalid phone numbers, can be a strong indicator of fraud.
2. High Volume of Applications from the Same IP Address
A large number of account sign-ups from the same IP address or device within a short timeframe can indicate automated activity or organized fraud efforts.
3. Masked Device Activity: High Application Volume with Altered Fingerprints
A high number of account sign-ups originating from the same device, even when using varied device fingerprints, can be a sign of sophisticated fraud tactics aimed at bypassing detection. Fraudsters often use tools to modify or mask device details to create multiple accounts without raising immediate suspicion.
4. Use of Synthetic Identities
Synthetic identities often include data that appears legitimate at first glance but can’t be verified as belonging to a real person.
5. Suspicious Email and Phone Number Patterns
Email addresses and phone numbers that follow unusual patterns or formats, such as disposable or temporary emails and VoIP numbers, can be indicators of fraud.
6. Rapid Account Creation Behavior
Fraudsters often create accounts quickly and in bulk, which can be detected through analysis of user behavior during the account opening process.
Incomplete or Redundant Information
Applications with missing or incomplete information or those that use generic placeholders (e.g., “N/A†for several fields) can indicate a fraudulent attempt.
8. Suspicious Geographic Locations
Applications originating from high-risk locations or places known for high levels of fraudulent activity can be a red flag.
9. Behavioral Red Flags During Onboarding
Behavioral analytics can reveal signs of fraudulent activity, such as erratic or unnatural interactions during the sign-up process.
10. Linked Accounts and Connections to Known Fraud
Accounts that share characteristics or links with previously flagged fraudulent accounts, such as similar email patterns or shared addresses, should be flagged for review.
11. High-Risk Account Opening Times
Fraudsters often operate during off-hours or when fraud detection teams are less active
Fraud’s Favorite Targets: The Most Vulnerable Industries for Fake Accounts
Certain industries are particularly vulnerable to account opening fraud due to their B2C nature and the services they offer. Sectors that provide free trials, sign-up bonuses, or promotional offers are especially exposed, as these incentives can be exploited by fraudsters creating multiple fake accounts. The appeal of easy onboarding with minimal verification processes makes it easier for fraudulent activities to take place. Recognizing the types of industries at higher risk helps businesses understand their exposure and implement more robust fraud prevention strategies:
1. Banking Account Opening Fraud
2. E-commerce and Online Retail
3. Telecommunications
4. Digital Services and Social Media fake Account Creation
6. Online Lending and Fintech Platforms
7. Gaming and Entertainment Platforms
8. Travel and Hospitality
9. Nonprofit and Charity Organizations
10. Subscription Services
11. Dating Apps
12. BNPL Services
Comparison with Account Takeover (ATO) Fraud
Definition and Core Differences
Motivations and Methods
Detection and Prevention
Advanced Techniques for Detecting and Preventing Account Opening Fraud
In the fight against account opening fraud (AO fraud), organizations must leverage a mix of advanced techniques and innovative technologies to detect and prevent fraudulent activities effectively. Below are the core strategies and tools that enhance these efforts:

By integrating innovative technologies like AI, behavioral analytics, and blockchain with proven prevention techniques such as enhanced KYC and MFA, organizations can build a robust, multi-layered defense against account opening fraud. These combined efforts are crucial for protecting businesses and maintaining user trust while minimizing disruptions to the customer experience.
Regulatory Landscape and Compliance Standards
Account opening fraud is a serious offense across various jurisdictions, with stringent regulations and penalties for both individuals and businesses involved. Below is an overview of the compliance requirements and associated penalties in Australia, the United Arab Emirates (UAE), and Europe.
Australia
United States
Europe
Asia
United Arab Emirates (UAE)
In all these jurisdictions, both individuals and businesses are held accountable for involvement in account opening fraud. Compliance with AML regulations is crucial to avoid severe legal consequences and maintain the integrity of the financial system.
Examples of fraud: From Australia to Europe
Fraudulent activities, particularly account opening fraud, continue to impact businesses and consumers globally. Examining real-world examples helps shed light on the methods employed by fraudsters and the resulting consequences. Understanding these cases is crucial for developing stronger security measures and proactive strategies to protect against such fraudulent schemes.
The Consequences of Account Opening Fraud for Businesses and Consumers
Account opening fraud (AO fraud) has far-reaching consequences that affect businesses, consumers, and the overall customer experience. Understanding these impacts can help organizations prioritize effective prevention strategies and maintain trust.
1. Consequences for Businesses
2. Consequences for Consumers
3. Impact on Customer Experience

Challenges in Detecting and Preventing Account Opening Fraud
Account opening fraud poses significant risks to businesses and consumers alike, making detection and prevention a priority. As fraudsters continually adapt their methods, understanding the landscape of account opening fraud is essential for developing robust defense mechanisms. This section will explore the main challenges that organizations face in combating this persistent threat.
1. Evolving Fraud Tactics
Fraudsters continuously develop new techniques and leverage advanced technologies, making it difficult for businesses to keep up with their adaptive strategies.
2. Limitations of Traditional Verification Methods
Basic KYC processes often fail to detect complex fraud types like synthetic identity fraud, as they rely on static and easily manipulated data.
3. Balancing Security with User Experience
Striking the right balance between effective fraud prevention and a seamless user experience is challenging, as more stringent measures can deter legitimate users.
4. Data Quality and Integration Issues
High-quality, integrated data is essential for robust fraud detection, but ensuring consistency and comprehensive data integration across systems can be difficult.
5. Resource Constraints
Smaller and mid-sized organizations may struggle with the financial and technical resources needed to deploy sophisticated fraud prevention tools and provide staff training.
Future Trends in Account Opening Fraud
As account opening fraud continues to evolve, staying ahead of emerging trends is crucial for businesses to maintain effective defenses. This section will explore anticipated developments in fraud tactics and prevention strategies, offering insights into what to expect in the changing landscape. By understanding future trends, organizations can better prepare for upcoming challenges and strengthen their approach to combating account opening fraud. Here's what to include:
1.Growing Use of Artificial Intelligence in the Fraud Battle
2. Growth in Synthetic Identity Fraud
3. Adoption of Biometric and Multi-Factor Authentication (MFA) Enhancements
4. Integration of Blockchain Technology
5. Tighter Regulatory Oversight
6. Advanced Behavioral Analytics and Anomaly Detection
7. Collaboration Between Industries and Governments
8. Enhanced Consumer Awareness and Education
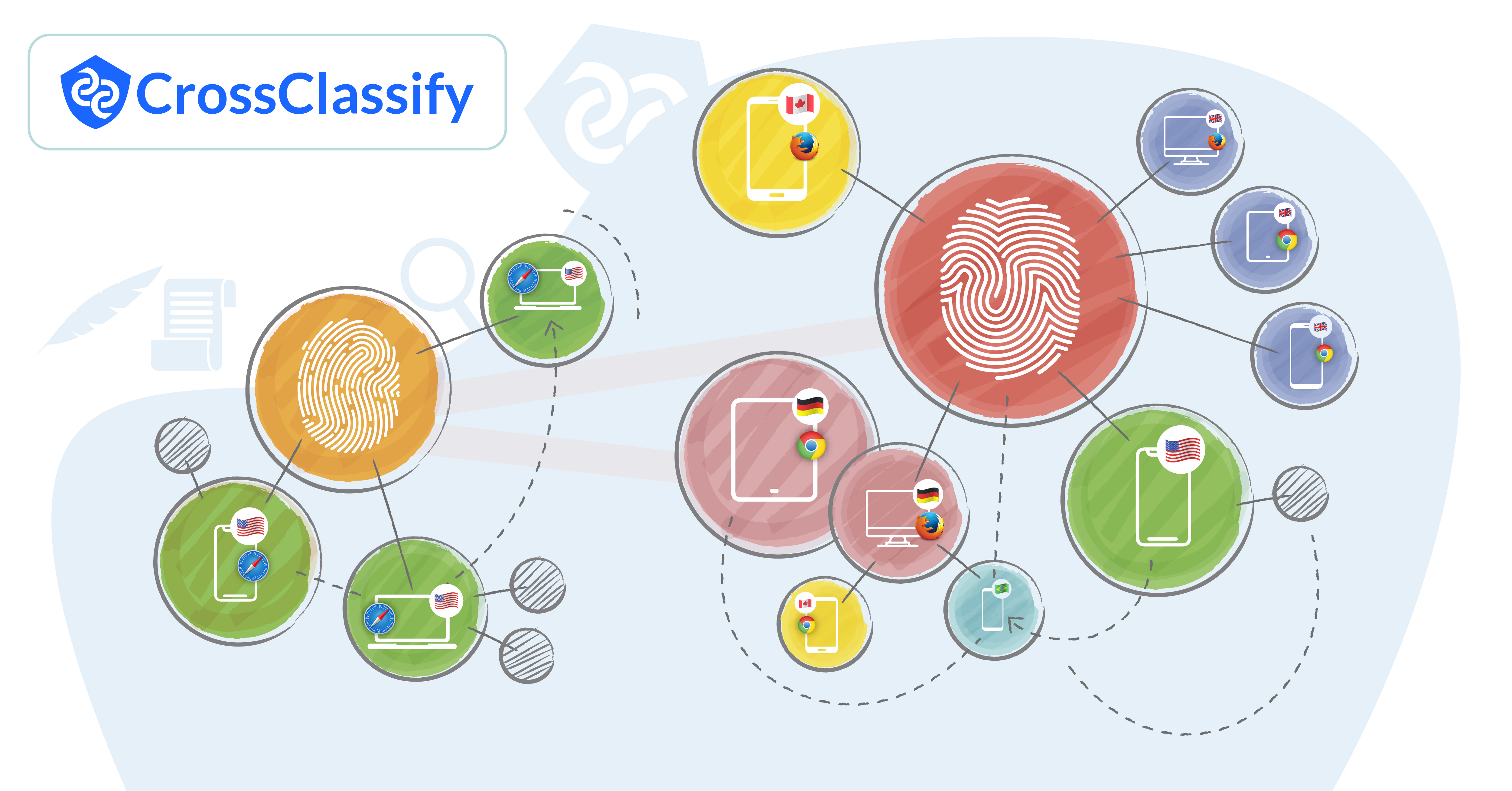
How CrossClassify Detects and Prevents Account Opening Fraud Effectively
To effectively detect and combat account opening fraud, organizations need to be equipped with advanced strategies and tools that can handle the complexity and scale of modern fraud tactics. The right solution should use AI-driven methods to accurately identify fraudulent activity without causing friction for legitimate users. This is where CrossClassify steps in as an essential tool, helping businesses stay ahead of account opening fraud through innovative detection and prevention strategies.
.jpg)
CrossClassify utilizes cutting-edge technology and proven approaches to safeguard against account opening fraud:
1. Synthetic Identity Fraud
With these comprehensive and proactive strategies, CrossClassify equips businesses with the necessary tools to detect and prevent account opening fraud, safeguarding their operations and maintaining user trust without disrupting legitimate user experiences.
Conclusion
Account opening fraud is a growing threat that impacts businesses, consumers, and industries across the globe. The increasing sophistication of fraudsters, driven by advancements in synthetic identity creation and widespread data breaches, underscores the urgent need for stronger, multi-layered fraud prevention strategies. High-risk sectors such as financial services, e-commerce, and telecommunications must adopt advanced solutions like AI-driven verification and behavioral analytics to protect against these evolving threats. Regulatory bodies worldwide are imposing strict compliance measures and severe penalties, emphasizing the importance of rigorous AML practices. By understanding the underlying causes, monitoring fraud trends, and implementing comprehensive detection and prevention techniques, organizations can better defend against account opening fraud and maintain consumer trust and security.
See How Protect Your Platform from Account Opening Fraud
CrossClassify uses AI and continuous behavior monitoring to detect and prevent Fake accounts, protecting your business processes

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Let’s Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required



