Last Updated on 30 Oct 2024
Account Takeover: Strategies for Prevention and Defense
Share in

Introduction to Account Takeover (ATO)
Account Takeover (ATO) is a rapidly growing cybercrime where unauthorized users gain access to legitimate online accounts through stolen credentials or social engineering tactics. In 2024, 24% of global consumers reported being victims of ATO, a sharp rise from 18% the previous year. In the U.S. alone, 29% of adults have experienced an ATO incident, costing victims an average of $180 each and often resulting in severe identity theft (Security.org). For businesses, ATO poses even greater risks, pushing the global average cost of such incidents to a record $4.88 million per breach in 2024 (based on the IBM Cost of a Data Breach Report 2024).
This surge in ATO attacks has made it a top concern for industries like e-commerce, financial services, and social media, where compromised accounts can lead to devastating consequences. As attackers become more sophisticated and automation tools proliferate, companies are urged to adopt comprehensive solutions that include multi-factor authentication, strong password management, and advanced security measures like behavioral analytics to detect anomalies in user behavior. This layered approach is essential to stay ahead of evolving threats and ensure effective protection against this growing form of fraud.
Let's now dive into the various aspects of account takeover to understand its impact and how to effectively combat it.
This surge in ATO attacks has made it a top concern for industries like e-commerce, financial services, and social media, where compromised accounts can lead to devastating consequences. As attackers become more sophisticated and automation tools proliferate, companies are urged to adopt comprehensive solutions that include multi-factor authentication, strong password management, and advanced security measures like behavioral analytics to detect anomalies in user behavior. This layered approach is essential to stay ahead of evolving threats and ensure effective protection against this growing form of fraud.
Let's now dive into the various aspects of account takeover to understand its impact and how to effectively combat it.
Account Takeover Variants: Synonyms and Related Concepts
Account takeover fraud comes in many forms and goes by various names depending on the techniques used and the targeted vulnerabilities. Understanding these different terminologies is key to recognizing how attackers exploit accounts and the specific risks they pose. Here are several common terms used to describe different variations of account takeover fraud:
- Account Hijacking: Refers to the unauthorized control of someone's account, typically through stolen credentials, allowing the attacker to act as the legitimate user.
- Unauthorized Account Access: Occurs when someone gains access to an account without permission, often through hacking or exploiting weak security measures.
- Credential Fraud: Involves using stolen or falsified credentials to access someone else's account, typically for financial gain or identity theft.
- Identity Takeover: When an attacker takes control of an individual's online identity, using it to commit fraud or steal sensitive information.
- Session Hijacking: A method where an attacker takes over a legitimate user's session, often by stealing session cookies or intercepting communication.
- Account Fraud: Refers to any fraudulent activity related to an account, such as unauthorized transactions or accessing sensitive data.
- Account Theft: Involves the stealing of an individual's account information and using it for fraudulent purposes.
- Compromised Account: A term used when an account has been accessed or manipulated by an unauthorized person.
- Identity Theft: Occurs when someone steals another person's personal information to commit fraud, often leading to unauthorized account access.
- Fraudulent Account Access: Refers to any unauthorized attempt to access an account with the intent to commit fraud.
- Breached Account: An account that has been illegally accessed due to a security breach or vulnerability.
- Hacked Account: Refers to an account that has been accessed or taken over by a hacker, often using malicious techniques.
- Illegitimate Account Access: Describes any unauthorized or unlawful access to an account for fraudulent or malicious purposes.
Understanding how account takeovers happen and what are the common strategies
Account takeover typically occurs through methods such as credential stuffing, where attackers use lists of stolen usernames and passwords from data breaches to access accounts, or phishing, where users are tricked into revealing their credentials. Here are the common strategies used for account takeover:
- Credential Stuffing: Attackers use lists of stolen usernames and passwords from previous breaches to try accessing accounts across multiple platforms, exploiting users who reuse passwords.
- Phishing: Cybercriminals trick users into giving up their login credentials through fake emails, websites, or messages that appear legitimate, leading to unauthorized account access.
- Social Engineering: This involves manipulating individuals into revealing confidential information, such as login credentials, by pretending to be a trusted entity.
- SIM Swapping: Attackers hijack a victim's phone number by transferring it to a SIM card they control, enabling them to intercept SMS-based two-factor authentication (2FA) codes and gain access to accounts.
- Malware: Attackers use malicious software, such as keyloggers or spyware, to capture a user's credentials and other sensitive data.
- Brute Force Attacks: Cybercriminals use automated scripts to guess passwords by rapidly attempting numerous combinations, often targeting accounts with weak or common passwords.
- Session Hijacking: Attackers intercept and steal session cookies or tokens to take over an active session without needing the user's credentials.
- Man-in-the-Middle (MitM) Attacks: Cybercriminals intercept communications between the user and a website, capturing login credentials and other sensitive information.
- Data Breaches: Large-scale breaches expose vast amounts of personal data, including login credentials, which are then sold on the dark web.
- Botnets: Networks of infected devices can be used to perform large-scale automated attacks, such as credential stuffing or brute force attacks.
Consequences of Account Takeover
Account takeover can have far-reaching consequences that extend beyond immediate financial losses, impacting both individuals and businesses in various ways. The following outlines some of the most significant repercussions of this growing threat:
- Financial loss:
ATO often leads to unauthorized transactions, fraudulent purchases, or withdrawal of funds. For individuals, this can result in drained bank accounts or stolen credit card information. For businesses, this could mean chargebacks, refund fraud, and lost revenue. - Data theft:
Once attackers gain access to an account, they can steal sensitive personal or business information. This could include login credentials, financial data, personal identification, or proprietary business information, which can be used for further fraud or sold on the dark web. - Reputational damage:
For businesses, ATO can harm their reputation, leading to a loss of customer trust. Customers affected by an account takeover may feel that the business failed to protect their data, potentially leading to loss of customers and damage to the brand's image.
One notable account takeover (ATO) incident occurred in the financial sector when several U.S. banks, including PNC Bank, experienced a surge in ATO cases from 2021 to 2022.This incident led to significant financial losses for both the customers and the financial institution, highlighting the widespread risk posed by ATO attacks. You can read the whole story from here. - Operational disruption:
Businesses may face operational downtime as they respond to and recover from an account takeover. This can involve restoring compromised accounts, investigating the breach, and enhancing security measures, leading to a temporary halt in business activities. - Legal and regulatory fines:
Businesses that suffer account takeovers, especially those handling sensitive customer data, may face legal consequences. Data protection regulations such as GDPR impose strict penalties on companies that fail to secure personal data, leading to fines and other sanctions. GDPR imposes fines based on the severity of the breach. For serious violations, fines can reach up to €20 million or 4% of the company's global annual turnover, whichever is higher. This would apply if the account takeover results in a significant breach of personal data or if the organization fails to implement adequate security measures (The Data Privacy Group GDPR Advisor). - Identity theft:
For individuals, an account takeover can lead to identity theft. Attackers can use stolen personal information to open new accounts, apply for loans, or commit other types of fraud under the victim's name. - Increased risk of further fraud:
Once an account is compromised, attackers can use it to gain access to other linked accounts or services. This can escalate into larger-scale fraud, particularly if attackers manage to infiltrate financial or enterprise systems through compromised credentials. - Emotional and psychological stress:
For individuals, dealing with the aftermath of an account takeover can be highly stressful and time-consuming. Restoring accounts, disputing fraudulent charges, and securing personal information can cause considerable emotional strain.
Common Red Flags Indicating an Account Takeover
Account takeovers can be difficult to detect until significant damage is done, but certain red flags often indicate that an account is at risk. Being aware of these signs is crucial for both individuals and organizations to identify suspicious activity and prevent potential financial and reputational harm. Below are some common indicators that an account might be compromised:
- Unusual Login Patterns
Frequent logins from new or unrecognized locations, varying time zones, or devices not previously associated with the user's profile are strong indicators of a potential account takeover. Additionally, if a legitimate user is suddenly logged out of their account while someone else logs in, it could mean an attacker has gained access and is actively using it. - Suspicious Changes in Account Details (e.g., Password or Email)
Any unexpected updates to key account information like the recovery email address, phone number, addresses or security settings can suggest that an attacker is attempting to lock out the original user. This is a common tactic to establish full control over the account and prevent the legitimate owner from reclaiming it. - Sudden Increase in Account Activity
A sharp rise in account usage, such as large financial transactions, sending out bulk messages, or excessive changes in stored data, indicates that the account is being exploited. Attackers often move quickly to transfer funds, purchase items, or send spam messages to contacts, maximizing damage before the breach is detected. - Notifications of Login Attempts from Different Locations/Devices
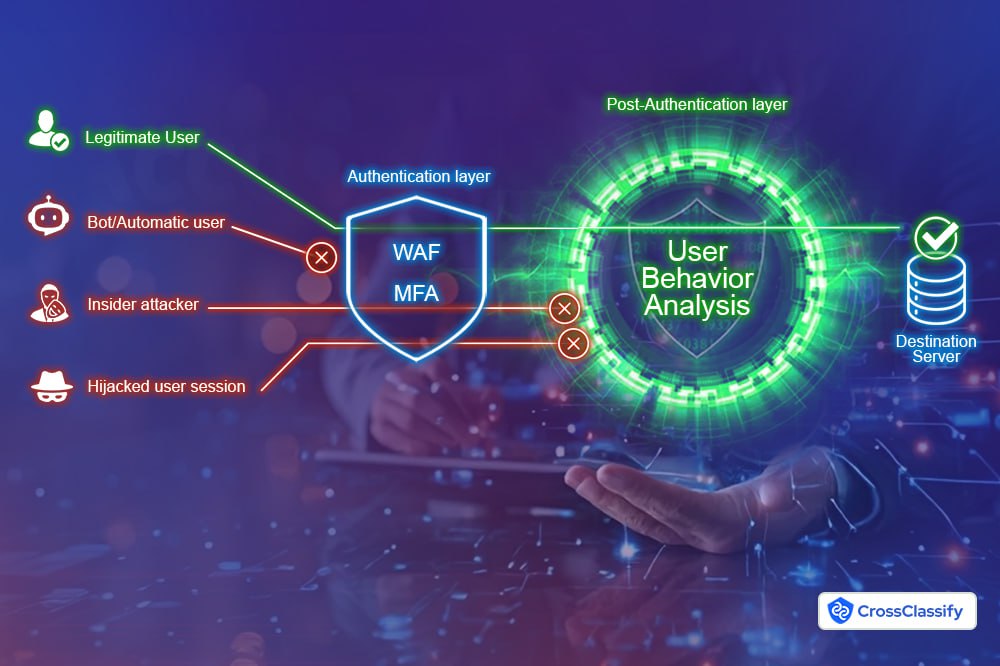
Alerts about attempted logins from unfamiliar locations or devices are a direct warning that someone might be trying to gain access. Even if these attempts fail, they highlight that the account is being targeted and may already be compromised. By monitoring these signs and employing additional security measures like behavioral analytics and multi-factor authentication, both individuals and organizations can detect account takeover attempts early and take prompt action to protect sensitive information.
Real-World Examples of Account Takeover Incidents
Here are some real-world account takeover examples, along with their financial losses:
- Australian Banking Sector Incident (Australia, 2024)
- Description: Australian banks were targeted by cybercriminals using SIM swapping and phishing tactics to gain access to customer accounts. Attackers intercepted one-time passwords (OTPs) to initiate unauthorized transactions.
- Financial Impact: Individual losses ranged from a few thousand dollars up to AU$15,000 per victim.
- E-Commerce Account Takeover in Australia (2023)
- Description: In this case, attackers targeted a large e-commerce platform in Australia by using stolen credentials to access multiple user accounts. The attackers made numerous fraudulent purchases, causing the company to suffer from substantial financial losses.
- Financial Impact: The estimated total loss exceeded AU$500,000, not including the associated chargeback costs.
- Source: (2023) (Security.org).
- Royal Bank of Scotland (RBS) Account Takeover Incident (UK, 2018)
- Description: In 2018, a woman in the UK lost over £4,000 ($5,000+) when a criminal took over her Royal Bank of Scotland account using a social engineering attack. The attacker successfully manipulated a customer service representative into transferring funds to an account under their control.
- Financial Impact: £4,318 in losses, which were later refunded by the bank.
- National Lottery Account Takeover (UK, 2016)
- Description: In 2016, the UK National Lottery suffered an account takeover attack where 26,500 player accounts were compromised. The attackers gained access to rich personal information and used it for further fraudulent activities.
- Financial Impact: Though the exact financial loss is unclear, the breach caused significant reputational damage to the lottery provider.
Future Trends in Account Takeover: A Continuous Battle of Innovation
As cybercriminals become more equipped with advanced technologies, the landscape of account takeover (ATO) is expected to evolve dramatically. To keep pace, fraud prevention and detection strategies are also becoming more sophisticated. The future of ATO will see both attackers and defenders leveraging cutting-edge technologies like artificial intelligence (AI), machine learning (ML), and behavioral biometrics in a continuous game of cat and mouse. While criminals are finding new ways to exploit emerging technologies, security tools are advancing just as rapidly to counteract these threats. Below, we explore three key trends that are shaping the future of ATO and the evolving tactics used by both attackers and defenders.

- Double-edged sword nature of AI/ML in ATO Attacks/Defense
AI and ML are transforming the nature of account takeover by enabling automation and scaling of attacks that are more efficient and harder to detect. Cybercriminals are leveraging AI to automate brute-force login attempts and mimic legitimate user behavior, making phishing attacks and social engineering schemes much more convincing. For instance, AI-powered bots are now capable of bypassing traditional security mechanisms, such as CAPTCHA systems, by simulating humanlike interactions.
As attackers continue to refine their techniques, defenses must evolve alongside them. Artificial intelligence (AI) and machine learning (ML) are essential for advancing behavioral analytics, enabling the detection of anomalies in real time. Security systems now have the capability to process vast datasets, such as login patterns, device usage, and geographic locations, to identify suspicious activity and prevent threats from escalating. Furthermore, adaptive authentication, which adjusts security protocols based on the perceived level of risk, is becoming more prevalent. These innovations ensure that security measures grow in sophistication to counter increasingly complex attacks. - Emerging Threats: Deepfake-Based Social Engineering
One of the most alarming emerging threats in ATO is the use of deepfake technology. Deepfakes leverage AI to create hyper-realistic video or audio impersonations, making social engineering attacks more deceptive and harder to detect. For example, an attacker could use deepfake audio of a trusted executive instructing an employee to share login credentials or authorize transactions, making the request appear legitimate. As deepfake technology becomes more accessible, its potential to facilitate sophisticated ATO attacks will increase, posing a serious challenge to traditional authentication systems.
In response, security tools are integrating more robust identity verification processes, such as multi-factor authentication (MFA) and voice or facial recognition, to counteract deepfake-based threats. These tools are being designed to spot subtle inconsistencies that can reveal a deepfake, providing an additional layer of defense against this emerging form of social engineering. - Evolution of Fraud Detection Techniques
To counter the growing sophistication of ATO attacks, fraud detection techniques are evolving rapidly. Behavioral biometrics—such as keystroke dynamics, mouse movement patterns, and even the way a user holds their device—are becoming essential in differentiating legitimate users from fraudsters. These techniques focus on how a user interacts with the system rather than relying on static credentials, making it extremely difficult for attackers to replicate genuine behavior.
Additionally, risk-based authentication (RBA) is emerging as a key trend. It dynamically assesses the risk level of a transaction or login attempt based on various factors, including device reputation, location, and historical user behavior. If a login attempt is deemed high-risk, the system automatically triggers additional verification steps, such as requiring a one-time password (OTP) or biometric confirmation. This evolving approach helps security systems stay ahead of increasingly sophisticated ATO tactics, offering more nuanced and layered security measures.
Account Takeover: A Growing Threat Across All Sectors
Account takeover (ATO) can occur in any application or service that involves user authentication, such as login and sign-up forms. While ATO is most commonly associated with high-value sectors like financial services, it is spreading to a diverse range of industries. Attackers target these platforms because each type of account holds unique data or resources that can be exploited for financial gain, reputation damage, or further cyber attacks. Below are the key domains where ATO is either prevalent or growing rapidly:
- FinTech (Financial Technology)
- Description: FinTech platforms, including digital wallets, trading apps, and online banking systems, are among the highest-risk targets for ATO. Attackers seek to access accounts to steal funds, conduct unauthorized transactions, or exploit user information for identity fraud. Due to the direct financial impact, successful attacks can lead to severe monetary losses and reputational damage.
- Why It's Targeted: High potential for financial gain and access to sensitive financial data makes FinTech one of the most attractive sectors for attackers.

- MedTech (Medical Technology)
- Description: MedTech platforms, such as patient portals and telehealth services, store highly sensitive personal and medical information. Attackers use ATO in this domain to commit insurance fraud, access prescription drugs, or steal private health data for extortion.
- Why It's Growing: The value of healthcare data on the black market is significantly higher than other types of personal data, making MedTech an increasingly lucrative target for attackers.
- LegalTech (Legal Technology)
- Description: LegalTech platforms, which are used by law firms to store client information, legal documents, and case details, are prime targets for ATO. A successful account takeover in this domain can lead to data breaches, sabotage of ongoing cases, or blackmail.
- Why It's Growing: The sensitive nature of legal data and its potential use for extortion or disruption of legal processes make LegalTech platforms attractive to cybercriminals.

- E-Commerce & Retail
- Description: E-commerce sites are frequently targeted due to stored payment information and user purchase histories. Attackers gain access to accounts to make unauthorized purchases, exploit stored payment data, or drain loyalty points.
- Why It's Targeted: Immediate financial rewards through fraudulent transactions and the resale of high-demand goods make this sector particularly vulnerable.
- Gaming & Gambling Platforms
- Description: Attackers target online gaming and gambling platforms to steal in-game assets, virtual currencies, or access sensitive payment details. These accounts can then be resold or used for laundering money through in-game transactions.
- Why It's Targeted: The rapid growth of digital gaming and the high value of in-game items create a lucrative market for cybercriminals.
- Social Media & Communication Platforms
- Description: Social media accounts are commonly targeted to harvest personal data, spread misinformation, or conduct identity theft. Attackers often use compromised accounts to send spam, launch phishing campaigns, or access other linked accounts.
- Why It's Targeted: Social media accounts hold valuable personal and professional information that can be leveraged for further attacks.
- Healthcare & Insurance Providers
- Description: Healthcare providers and insurance companies store detailed personal and medical records. ATO in this domain often involves using stolen data for insurance fraud or to gain access to medical services.
- Why It's Growing: The rising digitization of healthcare has increased the attack surface, making this sector more vulnerable to ATO attacks.
- Government & Public Sector Platforms
- Description: Government portals that provide citizen services, tax filing, and benefits management are being increasingly targeted. ATO attacks can result in unauthorized access to government benefits, identity theft, or sensitive data breaches.
- Why It's Growing: The valuable nature of personal data stored in these systems and the potential for financial and reputational harm make them appealing to attackers.
- Education Technology (EdTech)
- Description: EdTech platforms store sensitive information on students and faculty, making them targets for ATO to gain access to institutional systems or to conduct identity theft.
- Why It's Growing: The increased adoption of digital learning tools has expanded the attack surface, attracting cybercriminals.
- Travel & Hospitality
- Description: Travel and hospitality platforms are targeted for their stored payment information and rewards programs. Attackers use ATO to book travel services using stolen points or credit card details.
- Why It's Growing: The high frequency of online transactions in the travel sector creates multiple opportunities for attackers to exploit.
- Cryptocurrency Exchanges & Digital Wallets
- Description: Cryptocurrency platforms are frequently attacked due to their direct access to digital assets. A successful ATO can result in the theft of large sums of cryptocurrency, which can then be laundered through anonymous exchanges.
- Why It's Targeted: The pseudonymous nature of digital assets makes it difficult to trace stolen funds, making this a highly lucrative target.
- Subscription-Based Services
- Description: Platforms like streaming services and news subscriptions are targeted for credential sharing and resale. Compromised accounts are often sold on the black market for low-risk, recurring revenue.
- Why It's Targeted: Attackers exploit the low-security nature of many subscription services to gain access to user accounts.
Compliance Regulations and Fines for Account Takeover
Account takeover fraud is a significant concern for organizations, and compliance regulations are in place to protect personal data and ensure corporate accountability. Here are the key legal and compliance considerations, along with notable fines imposed for violations:
- GDPR (General Data Protection Regulation)
GDPR mandates strict data protection measures to prevent account takeover and unauthorized access:- Data Protection Impact Assessments (DPIAs): Organizations must conduct assessments to identify and mitigate risks associated with personal data processing.
- Data Breach Notifications: Data breaches must be reported to relevant authorities and affected individuals within 72 hours.
- Data Minimization and Encryption: Only necessary data should be collected, and it must be encrypted to prevent unauthorized access.
Fines Examples under GDPR:- Deutsche Wohnen SE: Fined €14.5 million in 2019 for improper data retention practices.
- Meta (formerly Facebook): Fined €110 million in 2017 for providing misleading
- ASIC (Australian Securities and Investments Commission)
ASIC enforces regulations to prevent account takeover and ensure transparency:- Corporate Governance: Companies must adhere to policies ensuring transparency and accountability.
- Internal Controls: Robust internal controls are required to detect and prevent account takeover attempts.
- Compliance Documentation: Companies must maintain and submit compliance documents upon request.
Fines Examples under ASIC:- Cetera Entities: Fined by the SEC for deficient cybersecurity procedures that led to email account takeovers.
- Cambridge Investment Research Inc.: Fined for similar cybersecurity failures.
- KMS Financial Services Inc.: Fined for inadequate cybersecurity measures.
- European Regulators (e.g., European Securities and Markets Authority - ESMA)
ESMA focuses on protecting investors and ensuring fair treatment during takeovers:- Equal Treatment: All security holders must be treated equally during takeover bids.
- Transparency: Sufficient information and time must be provided for investors to make informed decisions.
- Prohibition of Artificial Price Manipulation: Activities that artificially inflate or deflate security prices are prohibited.
Fines Examples by European Regulators:- European Commission: Fined Facebook €110 million in 2017 for providing misleading information during the WhatsApp takeover.
- EU Privacy Regulator: Fined Meta €91 million in 2019 for storing passwords in plaintext.
- Australian Legal Organizations
- Identify and Disrupt Act 2021: Agencies can take control of online accounts to gather evidence about criminal activity, applying to social media, online banking, and other accounts.
- Fraud Risk Assessment: Conduct fraud risk assessments following standards AS/NZ ISO 31000-2018 and AS 8001-2021.
Comprehensive Detection and Prevention of Account Takeover Fraud: User Challenges and Business Solutions
Account takeover (ATO) fraud is a complex threat that requires both individuals and businesses to implement a range of prevention techniques. However, many of the methods available to users come with drawbacks that can still leave accounts vulnerable. Businesses, due to their responsibility to comply with regulations and maintain their brand reputation, need to take proactive steps to detect and prevent fraud by leveraging more advanced tools.
User-Side Prevention Challenges:
While users can take steps to protect their accounts, these methods are not foolproof and often come with risks. For instance:
Business-Side Detection and Prevention:
To maintain compliance and protect their reputation, businesses must take a proactive approach to ATO fraud by implementing advanced detection methods:
To address these challenges, businesses should adopt advanced fraud detection tools. Techniques such as fraud scoring systems, monitoring login patterns, and tracking device fingerprints help identify anomalies in user behavior, such as unusual purchasing patterns or transaction frequencies.
Best Practices for ATO Fraud Prevention:
Given the complexity of ATO fraud, it's essential for both users and businesses to adopt best practices. For users:
User-Side Prevention Challenges:
While users can take steps to protect their accounts, these methods are not foolproof and often come with risks. For instance:
- Multi-Factor Authentication (MFA) provides an additional security layer but can be inconvenient for users, leading to low adoption rates. Moreover, SMS-based MFA is vulnerable to SIM swapping attacks.
- Strong, unique passwords are essential for account security, but users often struggle with remembering complex passwords or become frustrated with frequent updates, leading to weak or reused passwords.
- Being cautious of phishing attacks is critical, but phishing tactics are becoming more sophisticated, making it easy for even vigilant users to fall victim.
- Account alerts help detect suspicious activity, but too many notifications can cause alert fatigue, resulting in missed warnings.
Business-Side Detection and Prevention:
To maintain compliance and protect their reputation, businesses must take a proactive approach to ATO fraud by implementing advanced detection methods:
- Behavioral analytics and device fingerprinting can detect unusual login patterns and suspicious activity. However, these systems are not without challenges, such as false positives and evasion techniques by skilled fraudsters.
- Real-time monitoring and AI-driven fraud detection enable businesses to quickly detect and block account takeover attempts. Yet, these systems require continuous updates and training to stay effective, which can be costly and resource-intensive.
- Timely security updates and vulnerability patching reduce exposure to exploits, though delays in patching can still leave systems at risk.
- User education on security best practices is critical, but training can be expensive, and users may still make mistakes despite these efforts.
To address these challenges, businesses should adopt advanced fraud detection tools. Techniques such as fraud scoring systems, monitoring login patterns, and tracking device fingerprints help identify anomalies in user behavior, such as unusual purchasing patterns or transaction frequencies.
Best Practices for ATO Fraud Prevention:
Given the complexity of ATO fraud, it's essential for both users and businesses to adopt best practices. For users:
- Use strong, unique passwords and enable MFA for all accounts.
- Stay vigilant against phishing attacks and monitor accounts for suspicious activity regularly.
- Ensure devices and software are up to date to avoid security vulnerabilities.
- Implement strong authentication mechanisms like MFA or passwordless authentication.
- Use behavioral analytics and rate limiting tools to detect abnormal activity and prevent bot attacks.
- Ensure real-time monitoring and alerts are in place for immediate detection of suspicious activities.
- Monitor the dark web for credential leaks and notify users when their information is at risk.
- Ensure compliance with security regulations such as GDPR to avoid legal and financial penalties.
Who Are Responsible for Preventing Account Takeover Attacks?
Account takeover (ATO) protection and prevention require a coordinated effort from various roles within an organization, as well as individuals who manage their own accounts. Below are the key responsible persons involved in mitigating ATO risks:
- Chief Information Security Officer (CISO):The CISO oversees the overall security strategy of the organization, ensuring that robust policies and technologies are in place to prevent ATO attacks. They are responsible for implementing security frameworks and driving compliance with regulations.
- Security Operations Center (SOC) Teams:
SOC teams are responsible for monitoring systems in real time to detect and respond to suspicious activity. They play a critical role in identifying account takeover attempts early and mitigating threats before they cause harm. - IT Administrators:
IT administrators are responsible for managing the technical infrastructure, including setting up multi-factor authentication, ensuring security patches are applied, and maintaining firewall and intrusion detection systems. They ensure the technical defenses are in place to prevent ATO fraud. - Fraud Analysts:
Fraud analysts work to identify patterns and anomalies that could indicate account takeover attempts. They analyze data from fraud detection tools to flag abnormal behavior and investigate potentially fraudulent activities. - Data Privacy Officers (DPO):
DPOs ensure compliance with data protection regulations such as GDPR or the Australian Privacy Act. They are responsible for safeguarding personal data, reducing the risk of exposure that could lead to account fraud. - End Users (Individuals):
Users are the first line of defense in protecting their accounts. They must follow best practices like using strong, unique passwords, enabling multi-factor authentication, and being aware of phishing attempts to avoid compromising their accounts. - Customer Support Teams:
Customer support teams often handle account recovery and password reset requests. They must be trained to recognize social engineering attempts and follow strict protocols to avoid inadvertently granting access to attackers. - Vendors/Third-Party Security Providers:
Organizations may rely on third-party vendors for ATO protection tools, such as device fingerprinting, machine learning models, or AI-driven fraud detection. These vendors are responsible for maintaining the effectiveness of their solutions and staying ahead of new attack methods.
Challenges of Existing Off-the-Shelf Fraud Detection Tools
- User Friction/User Experience: Many tools, particularly those using two-factor authentication (2FA), create user friction by frequently requiring additional verification for every critical task. This disrupts user flow and can lead to frustration, reducing engagement or even causing user drop-off.
- Nightmare Integration: Integrating existing fraud detection tools with a business's existing systems can be complex, requiring significant time and technical resources. Customization, compatibility issues, and ongoing maintenance can turn the process into a nightmare, especially for businesses with limited technical capacity.
- Explainability/Interpretability: Most fraud detection systems lack transparency in how they detect suspicious activities. Businesses need clear, interpretable insights to act quickly and accurately when fraud is detected. The inability to understand why certain behaviors are flagged can lead to delays in response and less confidence in the tool's output.
- Cost: The cost of many fraud detection tools is prohibitively high, as they are often designed for large enterprises. Small and medium-sized enterprises (SMEs) and startups frequently find these tools outside their budget, limiting their access to effective fraud prevention technologies.
- Domain-Specific Limitations: Many tools are designed for general fraud detection and don't adapt well to industry-specific threats. Fraudulent patterns differ by sector, and tools that aren't tailored may overlook important signals. For instance, legaltech might encounter more session hijacking cases, whereas fintech may face payment fraud or account takeovers at a higher rate. General-purpose tools often fail to account for these industry-specific nuances.
- Scalability Issues: Some existing tools may struggle to scale effectively with a business's growth, leading to performance issues, slower detection times, or increased false positives as transaction volumes and user bases expand.
- Customization Challenges: Off-the-shelf solutions may not offer the flexibility needed to adapt to unique business models or workflows. Customizing these tools can be difficult and expensive, leading to suboptimal detection and prevention strategies that do not fully align with a company's needs.
- False Positives and Negatives: Many systems have high rates of false positives (flagging legitimate users as suspicious), which can frustrate customers and reduce trust. Conversely, false negatives (failing to detect real fraud) are equally problematic, allowing fraudulent actions to go undetected.
- Lack of Continuous Learning: Some fraud detection systems do not effectively adapt to evolving fraud patterns. Fraud techniques are constantly changing, and static systems that don't utilize machine learning or AI can quickly become outdated, leaving businesses vulnerable.
- Compliance Complexity: While some tools claim to help with compliance (e.g., GDPR, PCI DSS), they may not be fully equipped to handle the complexities of different regulatory environments. This can leave businesses exposed to fines and penalties if they fail to comply with industry-specific regulations.
Conclusion
In conclusion, account takeover (ATO) fraud is a rapidly growing threat, with cybercriminals using increasingly complex methods to exploit vulnerabilities. The magnitude of ATO fraud cannot be overstated, as it continues to result in substantial financial losses and reputational damage for businesses across the globe. To address these challenges, individuals must take proactive steps like enabling multi-factor authentication and using strong passwords, while businesses must adopt comprehensive security measures, including real-time monitoring and behavioral analytics. Given the complexity of ATO fraud, businesses can significantly improve their detection and prevention efforts by using specialized tools that leverage advanced fingerprinting, machine learning (ML), and AI. These tools help analyze abnormal behavior and suspicious activities in real time, enabling businesses to respond effectively to the ever-evolving threat landscape. Staying informed on the latest security trends and integrating advanced ATO detection solutions are essential to minimizing the impact of this growing threat.
See How Protecting Customers from the Growing Threat of Account Takeover
Ensure Continuous Security with Real-Time Account Monitoring

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Account takeover is a type of cyberattack where a fraudster gains unauthorized access to a user's account—usually by using stolen login credentials—to perform malicious actions like transferring funds, stealing data, or abusing services.
Account takeover fraud occurs when attackers exploit hijacked accounts to commit identity theft, financial fraud, or platform abuse. It’s one of the fastest-growing digital fraud threats across industries, including banking, eCommerce, and gaming.
ATO attacks often begin with leaked credentials found on the dark web. Cybercriminals use methods like credential stuffing, phishing, brute force, or malware to break into user accounts and move stealthily before detection.
A common example is when attackers access a user’s email or banking app, change credentials, and drain financial accounts. Others include exploiting SaaS accounts to steal business data or impersonating users for social engineering attacks.
Detection involves monitoring behavioral anomalies—such as login from unusual devices, IP changes, impossible travel patterns, or abnormal usage speed. CrossClassify’s ATO solution leverages device fingerprinting and AI-based behavior analysis to flag such risks.
ATO protection refers to the technologies and strategies that proactively identify, block, or mitigate unauthorized account access. CrossClassify uses real-time risk scoring, login anomaly detection, and bot defense to provide end-to-end ATO protection.
Identity theft involves stealing personal information to impersonate someone, whereas account takeover focuses on accessing and misusing an existing account. However, one can lead to the other in layered attacks.
Use strong, unique passwords, enable multi-factor authentication (MFA), and deploy solutions like CrossClassify that provide continuous monitoring, behavioral profiling, and device-level tracking to proactively prevent ATO.
Billions of leaked credentials make ATO low-effort and high-reward for attackers. As users reuse passwords across platforms and businesses digitize services, attackers increasingly exploit weak authentication and blind spots in fraud detection.
CrossClassify combines behavior analysis, device fingerprinting, risk scoring, and bot detection in a single platform. It doesn’t just react—it predicts and blocks suspicious activity before an account is taken over.Learn More →
Let’s Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required