Last Updated on 23 Jul 2024
Fraud and identity theft
Share in

Fraud and identity theft are major, rising concerns globally, affecting millions of individuals and organizations every year.
As citizens, we all experience identity theft and fraud attempts, in our everyday lives: That AI-voice message asking us to call that phone number. This parcel supposedly blocked at the post office without our immediate validation online. This email asking us to “login” urgently to fix a burning issue or stopped transaction.
Fraud and Identity Theft
Identity theft and fraud encompass a range of illicit activities where perpetrators use deceitful tactics to gain unauthorized access to personal data, admin credentials, financial accounts, or other sensitive information. The cost and prevalence of these activities can be staggering.
At high level, it can be split in two large sub-entities:
•
Traditional scam fraud
•
Identity theft fraud
These are very closely related, and overlap to a large degree but not entirely similar:
•
Traditional scam fraud rely on small amounts of data. It can be a scam text asking you to call a number, who is effectively a fraudster, pretending to be Microsoft support, bank admin, etc.
That fraudster may typically guide you to a fake bank login page for ex., so you enter your password/email, and will then use those to steal immediately from your account, knowing full well it will be locked down very soon.
- In this scenario, the personal data is somehow secondary: It is just a tool, in order to execute a fraudulent transaction, a direct theft.
Identity theft scams spend time to steal large amounts of your personal data to assume your online identity and conduct as many attacks under your name as possible. In this case, stealing from your bank account is only the beginning, learning more about you from your email inbox, contracting leases in your name, having you kicked out of your own home, accessing your social media, etc.
- In this (grimmer) scenario, the personal data is primary: It is with this, first and foremost, that the fraudster impersonates you online, builds a “synthetic person” profile, with whom they can then launch a wide variety of attacks, \stealing bank funds being only one of them.
Fraud and Identity theft - A huge, everyday problem
The 2022 Javelin cybersecurity report pegged the cost of identity related fraud for 2021, in the US alone, at USD$24Billion, affecting over 15Million Americans.
Interestingly, that same research organization observed a 15% drop in for 2022 in their 2023 report, which they attribute to the cumulative effect of user litigation, and raising awareness of cyber criminality among the user base.
However, the threats keep rising in volume and sophistication.

Cost and Prevalence of Identity Theft
Identity theft is a violent, high-impact type of cyber criminality, made even more dangerous by the fact that it is widely under-estimated.
In 2017 alone, in one single data breach, 148 Million US customers' data were stolen at Equifax, to name but one of the main breaches.
We will explore the direct impact of identity theft below, but let us behold for a second, the long term indirect cost of such breaches. The Equifax breach lone means that over one in two US adults had their credentials stolen, and mostly likely posted on the dark web.
Considering how much we all reuse passwords/email combinations across a variety of digital accounts, this kind of breach is truly catastrophic for the long term safety of any application user.
Our passwords/email combinations and their related 2FA (mobile phone number, email access) are increasingly easy to break, but our culture is still playing catchup, opening a gaping chasm of cybersecurity risk.
While specific global figures vary, identity theft remains a prevalent issue worldwide. The increasing digitization of financial services and personal data storage has only broadened the scope for potential theft.
The COVID-19 pandemic also saw an increase in identity theft incidents, as more people used digital and remote services.
Financial Impact of identity theft on victims
Identity theft results in significant financial losses each year.
For instance, the 2022 Identity Fraud Study by Javelin Strategy & Research reported losses amounting to nearly $52 billion in 2021 in the United States alone, affecting around 42 million U.S. consumers.
In 2022 again, in Australia this time, 32.8% of identity theft victims experienced credit card fraud, resulting in average out-of-pocket costs of $1,551 per victim. 29% of victims had their information misused for tax fraud or other benefits fraud.
Personal / Psychological impact of identity theft on victims
Another underrated aspect of identity theft if the occasionally substantial psychological impact visited on the victims.
Identity theft can have profound and long-lasting psychological impacts on victims, extending well beyond the immediate aftermath of the attack.
The persistent nature of identity theft, with new damages and fraudulent activities emerging months or even years later, can lead to ongoing emotional and mental health challenges.
88% reported severe emotional distress , lasting extended periods of time, way beyond that of the initial attack.
A key issue with identity theft is how “sticky” the attack is. Victims are often obliged to fight the cybercriminal for months, occasionally for years, as the cyber criminal keeps finding new accounts to break.
This structural lack of safety is very damaging to human psychology, fostering feelings of invasion, powerlessness, rage and depression.
Impact of identity theft to businesses:
The impact to businesses is, unsurprisingly, substantial to business-ending:
•
The average cost of a data breach for companies was $4.35 million in 2022, with breaches in the healthcare industry costing an average of $10.1 million.
•
In 2019, the average cost of a data breach involving identity theft was $201 per compromised record in the U.S.
•
Data breaches can severely damage a company's reputation, with 38% of consumers indicating they terminated their relationship with a business due to a breach.
•
Businesses face legal risks from regulatory fines (e.g. GDPR), class-action lawsuits, and the cost of providing identity theft protection services to impacted customers.
Overall, the 2022 Identity Fraud Study found that identity fraud losses increased by 83% compared to 2021, reaching $52 billion across nearly 43 million victims in the U.S. alone. The emotional toll and widespread financial devastation underscore the catastrophic nature of this crime for individuals and businesses alike.
Types and Techniques of Fraud
As for anything related to cybersecurity at large, fraud types around personal data and identity theft are dizzyingly numerous and varied in types.
Here are the top 20 below. This list is non exhaustive, new are added every year, and each type of fraud itself also evolves in sophistication with time.
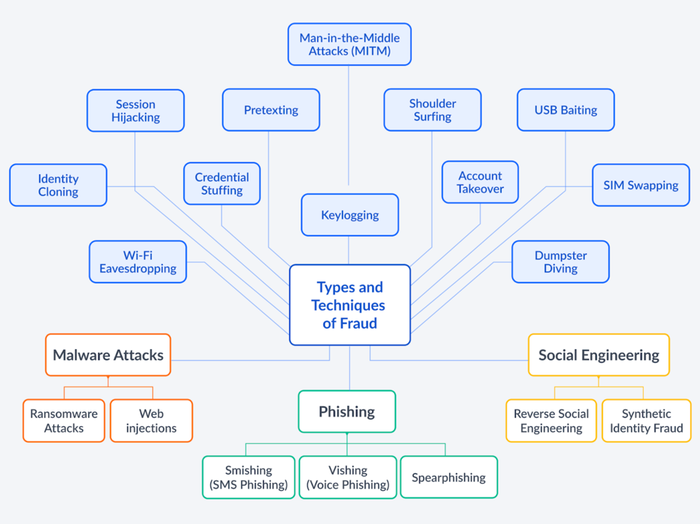
1.
Phishing: We all know this one, an older historical type of personal data attack. Sending emails that mimic reputable sources to trick individuals into disclosing personal information. Typically, most users can see through those. See also:
•
Smishing (SMS Phishing): Sending text messages that trick the recipient into providing personal information or downloading malware.•
Vishing (Voice Phishing): Using phone calls to trick individuals into revealing personal information or account details. This kind of attack has been at times popular but seems to be receding in prevalence as users become more aware of cyber risk and can typically detect the accent of the caller, or ask some validation questions back.
2.
Spearphishing: The difficulty level rises! Spearphishing is mostly an evolution from basic phishing gone ineffective. Gone are the emails with typos, leading to funny URLs and visibly faked landing pages. Spearphishing may only target a specific job title in a company, with a very specific message, leading to a sophisticated landing page, virtually unrecognizable from whatever bank or application they are spoofing. Spearphishing also generally uses more, better personal information than phishing, all in order to make the attack more contextual, and in this way, more credible.
3.
Session Hijacking: Extremely dangerous. Intercepting and exploiting a valid computer session to gain unauthorized access to information or services in a computer system, and/or take change credentials and completely kick out the valid user. If not identified early on by older cybersecurity protocols, a session hijacker will typically inflict severe damage to the valid account owner, and steal enough personal information to be able to easily log into other applications (keywords often repeat… addresses do not change… neither do emails…) Victims of session hijacking often do not realise what happened until an enormous damage has been done and they are already kicked out of multiple applications vital to their professional or personal life.
4.
Man-in-the-Middle Attacks (MITM): Intercepting communications between two parties to steal or manipulate data.
5.
Malware Attacks: Using software designed to harm or exploit any programmable device, service, or network to steal, encrypt, or delete data. This kind of attack is somewhat hybrid as it uses network exploits and general software issues to attack and inject malicious code, but the intent of the malicious code is not necessarily to destroy, rather, to gather, encrypt, steal, falsify and/or delete personal user data.
6.
Web injections: A similar type of attack, here the attacker injects malicious code into the application (often through web forms) or legitimate website, which then allows them to intercept data entered by the user into webforms. This kind of attack is particularly dangerous to users and online banking / shopping platforms, as successful fraudsters can quickly gather hugely valuable data (bank details including security numbers… login credentials…)
7.
Ransomware Attacks: A type of malware that encrypts the victim’s files, with the attacker then demanding a ransom to restore access. This is in essence, just a specific but common type of malware attack. By targeting known issues (unsafe plugins, network or software vulnerabilities) the cybercriminals disable access to the organization’s critical data and demand a ransom. Many of such attacks are from nation-states, and many are successful. These typically target organizations rather than individuals.
Once they have these, they use specialist software that will try to log into any odd thousands of online applications simultaneously, until they find a match and go into your account, one account found at a time. Typically very dangerous as the fraudster immediately disables valid credentials and replaces them with their own leading occasionally to extensive identity theft across many digital platforms.8.
Credential Stuffing: Using stolen account credentials to gain unauthorized access to user accounts through large-scale automated login requests. The fraudster must begin here by stealing two core data sets typically your keyword, and your email address it is matched to.
9.
Social Engineering: Manipulating people into performing actions or divulging confidential information.
Social engineering exploits psychology rather than technological vulnerabilities.
That great match on the dating site asking you your date of birth (for astrology) and your email only a few interactions in?... Might well be social engineering. That unrequested email inviting you to a glamorous conference all expenses paid, asking you to fill out the registration form? Maybe social engineering.10.
Reverse Social Engineering: A perverse evolution of the Social Engineering class of frauds. In this case the fraudster follows a slightly different but much more effective approach: He creates a scenario where the victim contacts them for assistance, lowering effectively most of their natural defiance and distrust with sharing important personal data online or strangers.
•
E.g. The fraudster will somehow engineer a technical issue on the computer of the user and communicate/position themselves as the official/solution to fix it. This is a fraud commonly used by fraudsters with older people who are not up to date with online technology.
11.
Identity Cloning: Extremely dangerous and traumatizing for the victims. Identity cloning is assuredly one of the most vicious types of cyber frauds. Here the fraudster does not only takeover accounts, he/she also now tries to assume entirely the identity of the victim in every day life. Using another person's information to assume his or her identity in daily life.
Legislation has caught up dramatically with identity theft in the last few years, but it remains a substantial issue, leading to truly catastrophic cost to the user.
How it works:
1.
Gathering/stealing personal data: Fraudsters involved in identity cloning start by gathering as much data as they can on their victim. This is not done online or digitally only, cybercriminals will often target mail boxes, dumpster dive or directly purchase some of the personal details on the dark web.
2.
Establishing a new identity: Using the information they already have, the fraudster now uses it to apply for new documents in the victim's name (driver’s license, social security card..) pretending to have lost them typically, voiding the previous identity in as many places as possible.
3.
Long term impersonation: Unlike most frauds which tend to be short-term, identity cloning can be a long game, with the fraudster living under the assumed identity for months or years.
Identity cloning is a particularly terrifying type of fraud, leaving victims exposed to enormous financial, existential and psychological damage.
Victims also often have to defend lawsuits when falsely implicated in crimes committed under their names by the fraudster.
12.
Synthetic Identity Fraud: Combining real and fake information to create a new identity, often used to open fraudulent accounts.
13.
Account Takeover: Unauthorized access and control of an online account belonging to someone else.
14.
SIM Swapping: Convincing a mobile provider to switch a phone number to a new SIM card, gaining control of the victim’s mobile communications.
SIM swapping is a highly deceptive type of fraud where the cybercriminal attempts to trick a mobile service provide into switching a victim’s phone number over to a SIM card he controls. The attacker poses as the victim and provides stolen personal information to pass identity checks.
If the cybercriminal is successful he can immediately take control of the victim’s phone number (calls, SMS) which he uses to bypass 2FA/MFA type solutions.
Since most users only use a few keyword variations and always the same email match, damage from SIM swapping can be extensive, as the fraudster will then try to hack other platforms and accounts of that user, takeover each, etc.
15.
Keylogging: Using malware to record a user’s keystrokes to capture their login credentials and other sensitive information.
16.
Wi-Fi Eavesdropping: Intercepting information sent over unprotected Wi-Fi networks.
17.
Pretexting: Creating a false scenario to persuade a victim to release information or perform an action. This is in effect a sophisticated form of social engineering in most cases.
The attacker may pose as a co-worker, police officer or bank official, do their best to mimic (by sharing some personal data they know, or context, to lower the suspicion level of the victim) the valid user.
They invoke an urgent need or a pressing scenario, to get more information.
“I’m locked out of our Cloud during the presentation to the CEO! Can you remind me the keyword just this one time so I can get back in?”
A lot around the pretexting frauds hinges on the “chat” and charisma of the fraudster, and it is a technique used for many other separate but related frauds.
18.
Dumpster Diving: Searching through trash to find bills or other paper containing personal information. This is not so much a fraud as such, as much a fraudulent way to acquire personal information for a variety of fraudulent goals.
19.
Shoulder Surfing: A very simple one, but also underrated in its effectiveness: The direct observation, such as looking over someone's shoulder, to get information like ATM PINs.
20.
USB Baiting: Dropping infected USB sticks in accessible areas, hoping individuals will use them on their computers, unwittingly installing malware.
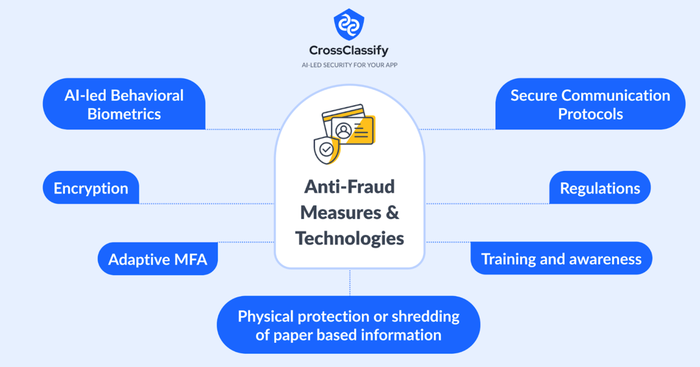
Preventive Measures and Technologies:
Discuss security measures that can be adopted to protect and prevent account fraud, including:
•
Physical protection or shredding of paper based information
•
Adaptive MFA (Multi-Factor Authentication)
•
Encryption
•
AI-led behavioral biometrics
•
Secure communication protocols
•
Impact of training and awareness: Since most of these frauds rely heavily on user interactions, training staff and users on the current state of cybersecurity threats, and what protocols you are implementing to protect can help lower cybercrime.•
Impact of Regulations: Review how regulations like GDPR and CCPA influence strategies for combating identity theft and fraud. Adherence to data protection regulations such as GDPR in the EU and CCPA in California helps organizations strengthen their defenses against data breaches and identity theft.
Conclusion
Identity theft and personal data based frauds in general, do not only causes immediate financial loss but can also have long-term effects on victims’ financial health and stress levels.
Its evolving nature requires constant vigilance and adaptation of security measures to effectively mitigate the risks.
Scalability, proactive measures, early intervention and user innovative technologies to provide holistic account and application protection are required to combat modern fraud and secure personal and organizational data.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
