Last Updated on 29 Oct 2024
Device Fingerprinting: Revolutionizing Digital Security and Beyond
Share in

Key Notes
•
Accuracy and Adaptability:Learn how device fingerprinting uses dynamic and static attributes to excel in fraud prevention and user authentication.•
Privacy Compliance: Understand the importance of aligning device fingerprinting practices with regulations like GDPR and CCPA to build user trust.•
Future Readiness: Explore how integrating AI, IoT, and privacy-enhancing technologies ensures long-term effectiveness in combating security threats.
Introduction to Device Fingerprinting
In 2024, cybercrime is projected to cost the global economy approximately $9.5 trillion USD annually, underscoring the escalating threat to businesses worldwide (Cybersecurity Ventures).
To combat these challenges, device fingerprinting has emerged as a pivotal technology, with its adoption growing at an annual rate of 15% across various industries. Notably, over 70% of financial institutions and 60% of e-commerce platforms have implemented device fingerprinting to enhance security measures, improve user authentication, and streamline customer experiences (Cobalt).
Device fingerprinting creates a unique digital identifier for a device by analyzing a combination of its attributes.This technology's significance spans multiple sectors, including finance, healthcare, and online services. By uniquely identifying devices accessing their systems, businesses can detect anomalies, prevent unauthorized access, and ensure secure transactions. Whether it's protecting patient data in healthcare, securing online banking platforms, or enhancing the checkout process in e-commerce, device fingerprinting is reshaping digital security standards. For companies aiming to stay ahead in a competitive market, adopting this technology is not just beneficial—it's essential.
To combat these challenges, device fingerprinting has emerged as a pivotal technology, with its adoption growing at an annual rate of 15% across various industries. Notably, over 70% of financial institutions and 60% of e-commerce platforms have implemented device fingerprinting to enhance security measures, improve user authentication, and streamline customer experiences (Cobalt).
Device fingerprinting creates a unique digital identifier for a device by analyzing a combination of its attributes.This technology's significance spans multiple sectors, including finance, healthcare, and online services. By uniquely identifying devices accessing their systems, businesses can detect anomalies, prevent unauthorized access, and ensure secure transactions. Whether it's protecting patient data in healthcare, securing online banking platforms, or enhancing the checkout process in e-commerce, device fingerprinting is reshaping digital security standards. For companies aiming to stay ahead in a competitive market, adopting this technology is not just beneficial—it's essential.

What is device fingerprinting?
Imagine Sarah, a frequent online shopper, logging into her favorite e-commerce platform from her laptop. Over time, the platform has learned to recognize her device based on its unique characteristics, such as the browser version, and screen resolution. One evening, someone tries to access Sarah’s account from a different device in another country. The platform immediately detects the mismatch between the new device’s fingerprint and Sarah’s usual profile, triggering an alert and requiring additional authentication to ensure her account remains secure.
This process exemplifies device fingerprinting, a technology that identifies devices based on a combination of unique attributes such as operating system, browser settings, plugins, time zone, and more. By creating a distinct “fingerprint” for each device, this method allows organizations to track and authenticate users without relying on traditional cookies, ensuring enhanced security and user experience. You can explore how device fingerprinting work fromhere.
This process exemplifies device fingerprinting, a technology that identifies devices based on a combination of unique attributes such as operating system, browser settings, plugins, time zone, and more. By creating a distinct “fingerprint” for each device, this method allows organizations to track and authenticate users without relying on traditional cookies, ensuring enhanced security and user experience. You can explore how device fingerprinting work fromhere.
The Limitations of Traditional Tracking: Why Device Fingerprinting Became Essenti
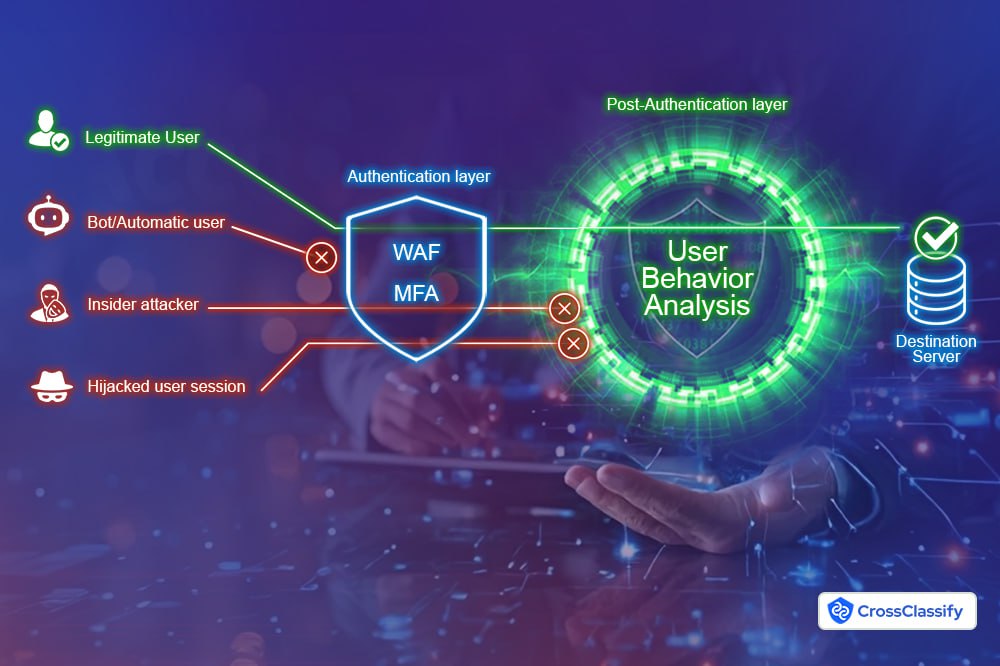
Before the advent of device fingerprinting, fraud detection relied heavily on traditional methods such as IP-based monitoring. These methods offered limited visibility and were easily exploited by fraudsters who could mask their IP addresses, use proxy servers, or change networks to avoid detection. This lack of precision made it difficult to trace the origin of suspicious activities or distinguish between legitimate users and malicious actors.
Without the nuanced insights provided by device fingerprinting, detecting complex fraud schemes—such as fake account creation, unauthorized transactions, or account takeovers—was a significant challenge. Businesses were left with fragmented data, leading to inefficiencies in identifying threats and an increased risk of financial losses and reputational damage. Unlike static IP tracking, device fingerprinting captures detailed information about the device itself—such as browser configurations, operating system details, and hardware characteristics—to create a unique “fingerprint” for every device. This advancement significantly reduced fraud opportunities by allowing systems to uniquely detect each device globally and accordingly, lead to improvement in identification of suspicious behavior and detect anomalies in real-time.
Without the nuanced insights provided by device fingerprinting, detecting complex fraud schemes—such as fake account creation, unauthorized transactions, or account takeovers—was a significant challenge. Businesses were left with fragmented data, leading to inefficiencies in identifying threats and an increased risk of financial losses and reputational damage. Unlike static IP tracking, device fingerprinting captures detailed information about the device itself—such as browser configurations, operating system details, and hardware characteristics—to create a unique “fingerprint” for every device. This advancement significantly reduced fraud opportunities by allowing systems to uniquely detect each device globally and accordingly, lead to improvement in identification of suspicious behavior and detect anomalies in real-time.

Device Fingerprinting vs. Browser Fingerprinting vs. Cookies: What Sets Them Apart?
Understanding how device fingerprinting, browser fingerprinting, and cookies differ is essential for grasping their roles in online tracking and security. Here’s a concise comparison:
•
Device Fingerprinting: Creates a unique device identifier using hardware and software attributes (e.g., OS, device model, plugins). It's robust, consistent across browsers/sessions, and ideal for fraud prevention.•
Browser Fingerprinting: Focuses on browser-specific details (e.g., user agent, fonts, version). While unique, it's less reliable due to disruptions from browser updates or changes.•
Cookies: Small data files stored in browsers for session tracking and personalization. They're fragile, browser-specific, easily deleted, and less effective under privacy regulations like GDPR.•
Takeaway: Device fingerprinting excels with its persistence and reliability, making it a critical tool for user identification and fraud prevention.
Challenges Solved by Device Fingerprinting
Device fingerprinting offers advanced solutions to key challenges in digital security, including fraud prevention, user authentication, and handling dynamic device environments:
Fraud Detection and Account Takeovers : By creating unique device identifiers, it detects activities like multi-account creation, unauthorized logins, and payment fraud. Example: Banks use it to flag repeated fake accounts from the same device or unrecognized logins requiring additional verification.
Device Sharing and Device Dynamic Configuration: Recognizes legitimate users on shared or updated devices by analyzing broader device attributes and user behavior. Example: In e-commerce, it identifies unusual patterns, reducing fraud while allowing seamless experiences for genuine users.
Overcoming Cookie Limitations: Tracks devices persistently, unaffected by cookie deletion or privacy restrictions.
Detecting Anomaliesand Patterns: Identifies patterns like multiple accounts from one device or unusual activity spikes, enabling proactive fraud prevention.
Improving User Experience and Security Compliance: Reduces false positives and adapts to routine device changes (e.g., updates) while ensuring privacy compliance with GDPR/CCPA.
Device fingerprinting is a powerful tool for securing platforms against evolving threats while maintaining user trust and regulatory adherence.
Fraud Detection and Account Takeovers : By creating unique device identifiers, it detects activities like multi-account creation, unauthorized logins, and payment fraud. Example: Banks use it to flag repeated fake accounts from the same device or unrecognized logins requiring additional verification.
Device Sharing and Device Dynamic Configuration: Recognizes legitimate users on shared or updated devices by analyzing broader device attributes and user behavior. Example: In e-commerce, it identifies unusual patterns, reducing fraud while allowing seamless experiences for genuine users.
Overcoming Cookie Limitations: Tracks devices persistently, unaffected by cookie deletion or privacy restrictions.
Detecting Anomaliesand Patterns: Identifies patterns like multiple accounts from one device or unusual activity spikes, enabling proactive fraud prevention.
Improving User Experience and Security Compliance: Reduces false positives and adapts to routine device changes (e.g., updates) while ensuring privacy compliance with GDPR/CCPA.
Device fingerprinting is a powerful tool for securing platforms against evolving threats while maintaining user trust and regulatory adherence.
Conclusion
Device fingerprinting has emerged as a transformative tool in digital security, offering exceptional precision in fraud detection, user authentication, and anomaly tracking. Its unique ability to identify devices has become indispensable across industries such as finance, healthcare, and e-commerce. Unlike traditional tracking methods, which often fall short in today’s dynamic digital landscape, device fingerprinting stands out for its robustness and adaptability.
As the technology continues to evolve, businesses must implement it thoughtfully, balancing innovation with compliance to privacy regulations like GDPR and CCPA while fostering user trust. In an increasingly complex cyber environment, adopting and refining device fingerprinting is not merely an option—it’s an essential step for staying secure and competitive.
As the technology continues to evolve, businesses must implement it thoughtfully, balancing innovation with compliance to privacy regulations like GDPR and CCPA while fostering user trust. In an increasingly complex cyber environment, adopting and refining device fingerprinting is not merely an option—it’s an essential step for staying secure and competitive.
See How Stop fraud with unique device identification
Create powerful device profiles to uncover hidden threats instantly

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Device fingerprinting is a technique used to identify and track a device based on its unique attributes—like browser type, OS, screen resolution, and installed fonts—without relying on cookies or user credentials.
A device fingerprint is a unique profile generated from a combination of hardware and software attributes. It's used to recognize returning users or detect anomalies during login, account creation, or transactions.
It collects non-invasive information (like browser version, IP, plugins, and timezone), hashes it into a unique identifier, and compares it against historical fingerprints to assess risk or consistency.
It helps detect suspicious behavior, such as bots, account takeovers, or multiple fake accounts from a single device. CrossClassify uses it to build persistent digital identities across sessions—even when IPs or accounts change.
An example is when a user tries to sign in from a known account but with a new fingerprint (e.g., new device or emulator). The system flags this as a high-risk event or blocks the request.
Mobile fingerprinting considers sensors, device models, and mobile browser properties. It’s more dynamic due to OS updates and app sandboxing but still effective when combined with behavioral signals.
While not foolproof, modern device fingerprinting—especially when combined with behavioral analysis and AI—achieves high accuracy in detecting anomalies and preventing unauthorized access or automation attacks.
You can embed CrossClassify’s fingerprinting API into your checkout, login, or sign-up flows. It passively collects data, scores the session risk, and sends fraud alerts or blocks transactions based on the fingerprint.
Yes, when implemented transparently and with privacy controls. CrossClassify anonymizes fingerprint data and doesn’t track personal behavior across unrelated domains, making it compliant with GDPR and similar regulations.
CrossClassify goes beyond basic fingerprinting by combining it with real-time behavioral analysis, anomaly detection, and adaptive risk scoring. It helps secure your app against bots, account abuse, and fake identities.
Let’s Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required