Last Updated on 30 Jul 2024
Account fraud
Share in

Cybersecurity has always been a fast evolving field, countering a mutating, fragmenting threat. This threat has been accelerating since the advent of Large Language Models (LLM) and Generative AI.
Fraudsters have been quick to leverage the new possibilities of AI when it comes to generating near-perfect imitations of landing pages (for phishing) or data theft (Gen AI voice messages asking for credentials “verification” etc.)
As a result, a class of frauds that has grown exponentially of late is account fraud: account hijacking, new account opening fraud, identity theft, data harvesting, blackmail and extortion.
What are the typical goals of account fraud cyber criminality?
Account fraud is a huge class of cyber criminality, rapidly growing, and made ever more sophisticated by the growing use of AI by bad agents. We dedicate a longer focus on this class of threats here by looking at types of “goals” (costs, risks) they aim for.
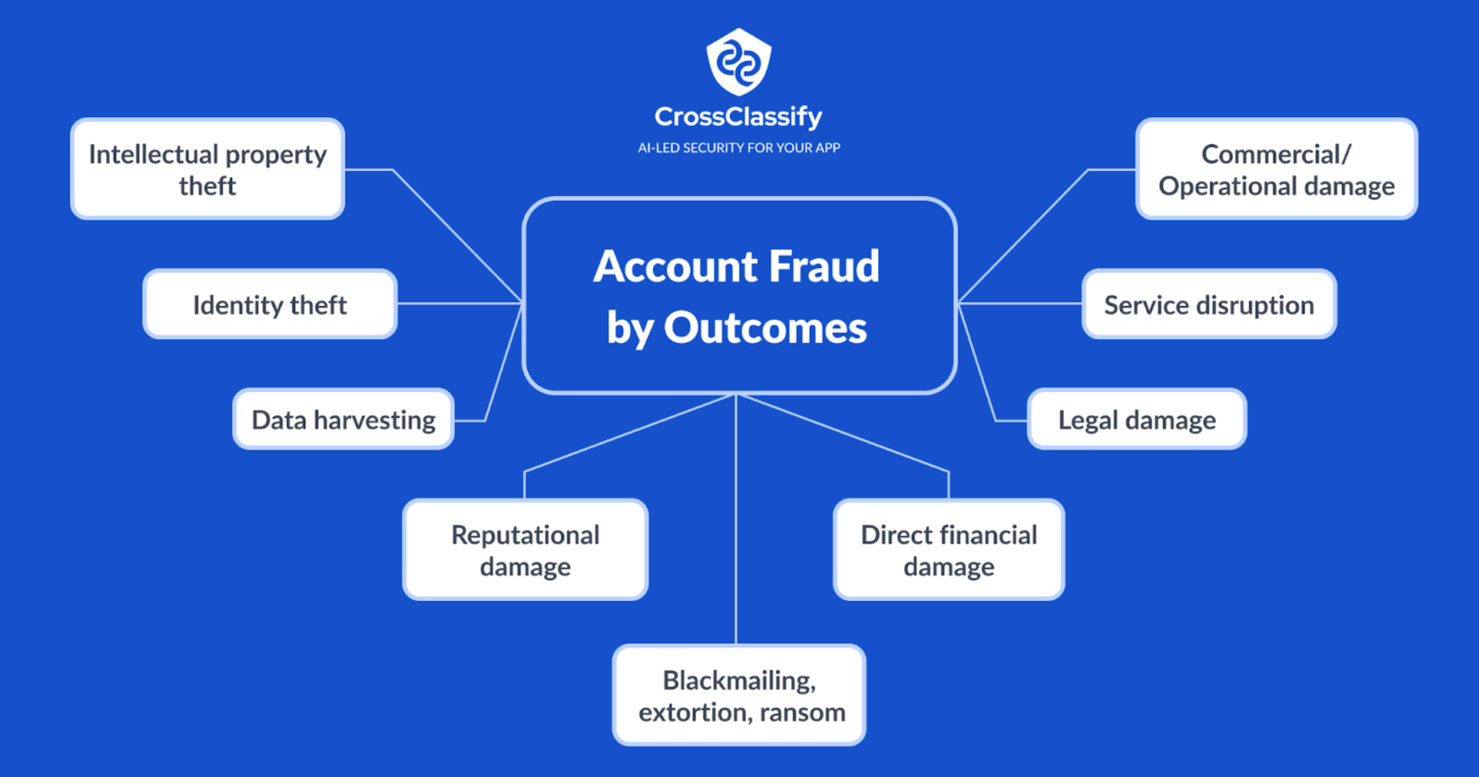
The “outcomes” sought by cyber criminals involved in account fraud, can be very different:
•
Identity theft: using the first account taken over to break as quickly as possible in as many other online accounts of the victim. Extreme identity theft can last months or years, involve real estate deed fraud, fraudulent loans or cash withdrawals.
•
Data harvesting: This overlaps with identity theft but differs in the sense that data is here also considered “as such” for the value it can be sold for to other cybercriminals, on the dark web, etc. Data once harvested is both kept by the cybercriminal for their own use as well as sold to other cybercriminals.
•
Direct financial damage: In this scenario the cybercriminal hacks into your bank/fintech account, and directly steals from their own to their benefit, by making as many transactions as possible. They tend to know the maximum amount of $ they can withdraw without triggering an extra 2FA and will max it out, every 24h, as long as their access is maintained.
•
Commercial/Operational damage: Cybercriminals are very active in the corporate world, something obvious in “New account opening” fraud (NAO fraud) for ex. NAO fraud works by creating as many accounts on a platform as possible, that the cybercriminal will later use to inflict commercial/legal damage.
They may redeem a 50% offer limited in theory to one per user, across x1000 accounts causing legal and commercial damage. Cybercriminals in control of hundreds of accounts can also easily skew usage data, blurring strategic application metrics from the valid owner.•
Legal damage: Related to the commercial damage above, account fraud can also be leveraged by the cybercriminal to inflict legal costs and damage. Cybercriminals in control of hundreds of accounts can lead the platform owner into non-compliance, acquire proof and create further legal/regulatory headaches.
•
Service disruption: Cybercriminals often attack critical services, whether in medtech, lawtech, government, critical infrastructure or fintech. They do this both because the data is typically of higher value but also because they can inflict more ongoing damage to the legitimate owner by denying online service.
Lawtech operates around extremely rigid timeframes, and cannot afford long without specialist apps and the data they contain.
Denial of service also represents an extreme, ongoing reputational damage from unhappy clients, many of whom will not return. This is often related to sabotage, or ransomware (below).•
Reputational damage: Here also cybercriminals tend to favor industries where data is a) critical to BAU operations b) extremely high value, such as lawtech, fintech and medtech. Here cybercriminals may simply use accounts to post inappropriate content, conduct illicit activities that tend to hurt valid users of the platform.
Occasionally it includes directly posting content (on boards, pages) indicating how easy the platform has been to hack into. The medium and the message overlap in that case: It is what it looks like, a platform that has been hacked.
Reputational damage in extreme cases can be business-ending in the short term, or longer term.•
Intellectual property theft: Gaining access to valid accounts can also be leveraged to gain critical intellectual property such as designs, code, algorithm formulae.
The cybercriminal can then either/or sell the IP and trade secrets directly, or also leverage them further against the company.•
•
Blackmailing, extortion, ransom:This whole class of account fraud is particularly ugly and brutal and relies to a point on human psychology and manipulation.
The cybercriminal acquires access to an account, takes over and kicks out the valid owner, demanding ransom for resumed access. This is common, and highly effective when carried on critical applications.
These account frauds are versatile and target both the account (and access to) as well as the data it contains. If a company has proof their proprietary data has been indeed accessed, they probably have a redundant copy somewhere.
So, continued access to the service is not threatened. However the extremely high value data itself is now compromised and their interest is ensuring at least that it does not get leaked to competitors.
Account fraud: Different types and mechanics
Account fraud has been managed historically through the use of keywords. When those became too weak alone to protect account security, multiple-factor-authorization (MFA, or 2FA) was introduced.
At log in, the user gets a SMS asking them to enter the code that they only can hold since it is sent to a device.
However this is now fast becoming obsolete. And a large part of the cybersecurity stakes, and risks, lies in the false sense of security that 2FA or MFA creates.
In simple terms, if you ever click that link in this SMS asking you for an immediate keyword update or the parcel won't be delivered, someone on the other end now has a) your mobile number and b) your login credentials.
No particular 2FA can protect against that kind of attack, or in plainer terms yet, if the cybercriminal directly buys fraudulent tokens on the dark web. Classic MFA is fast becoming obsolete and riskier for users as well as for application security managers relying only on that protocol.
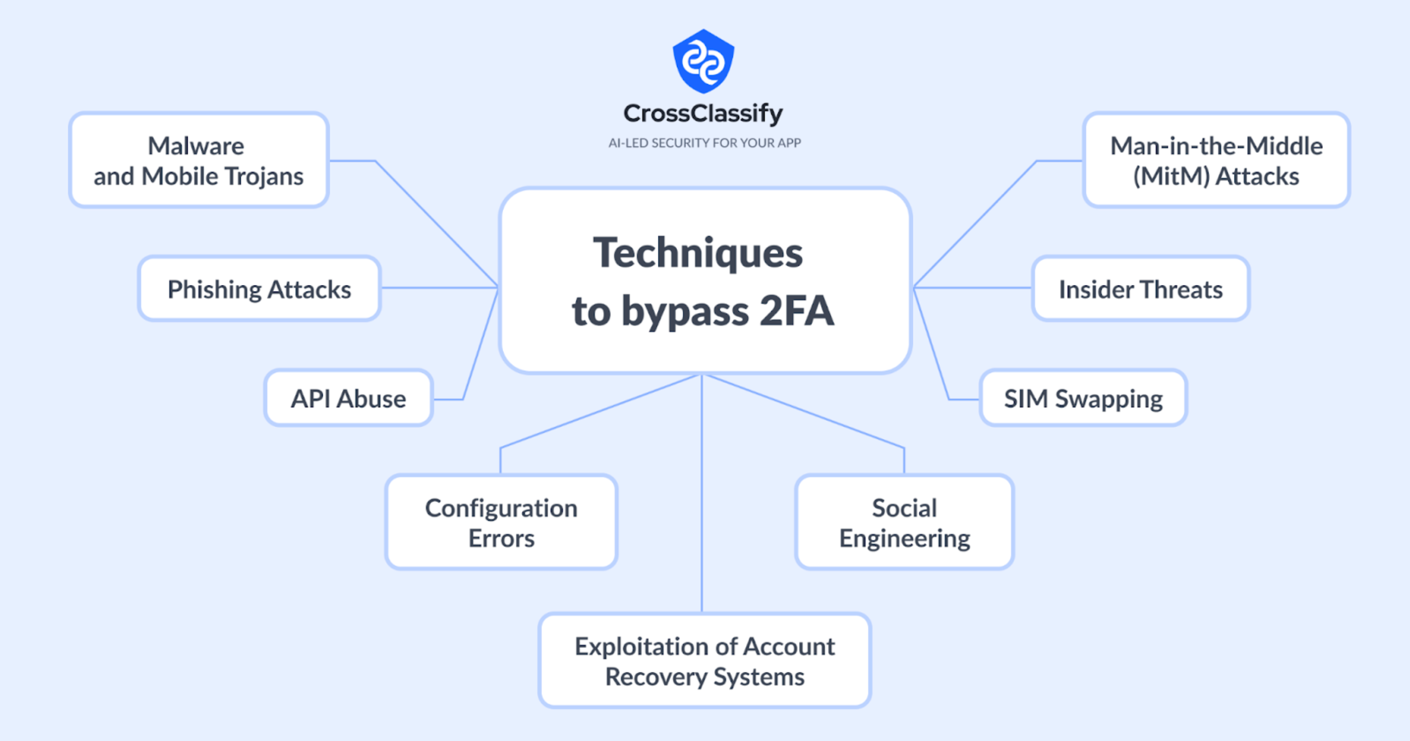
Cyberfraudsters employ several techniques to bypass two-factor authentication (2FA), even when they have already obtained a user's login credentials. Here are some common methods:
•
Phishing Attacks: Fraudsters often use phishing schemes to trick users into providing their 2FA codes. They might send a fake security alert prompting the user to enter their credentials and the 2FA code on a website that mimics the legitimate one.
•
Man-in-the-Middle (MitM) Attacks: Here the attacker stays between user and service, intercepting 2-way communications. E.g. when a user logs into a service, the attacker captures both the password and the 2FA token in real-time, allowing them to use these details before the token expires.
•
SIM Swapping: This involves the attacker convincing the mobile carrier to switch the victim's phone number to a SIM card controlled by the attacker. Once done, any SMS-based 2FA codes are sent to the attacker's device.
•
Exploitation of Account Recovery Systems: Sometimes, account recovery processes are less secure than the login process and might not require 2FA. Attackers may exploit these weaker paths to gain access without needing to bypass the 2FA.
•
Malware and Mobile Trojans: Some malware is specifically designed to steal 2FA tokens by infecting the user’s device. Mobile banking trojans, for example, can intercept or forward SMS messages containing 2FA codes to attackers.
•
Social Engineering: Attackers sometimes use social engineering tactics to persuade users or customer support representatives to disable 2FA on accounts or to provide the necessary information to bypass it.
•
API Abuse: As SaaS applications frequently rely on APIs for communication between services, attackers exploit insecure APIs to access sensitive data, manipulate services, or cause disruptions. This includes attacks such as unauthorized access, data leakage, and denial of service through API endpoints.
•
Configuration Errors: Misconfigurations of security settings in the cloud or within the application itself can leave the system vulnerable to attacks. Common issues include improper access controls, unsecured storage buckets, and default credentials.
•
Insider Threats: These attacks are perpetrated by individuals within the organization who have legitimate access to the system. Malicious insiders can misuse their access to steal data, sabotage systems, or facilitate external breaches.
Account fraud: AI protection and future trends
In order to make an application secure it is vital to follow best practices such as strict validation of data entry, encrypting data in transit and at rest, protecting against data loss.
Following a policy of regular updates for software as well as network hardware lowers risk for known vulnerabilities.
1.
AI & Application Security: Use case and leverageWe use all sorts of cybersecurity tools to protect clients apps and digital operations (advanced statistics, conditional logic, etc.) However, leveraging AI represents another class of benefit: Adaptive cybersecurity. Apps can be monitored in real time, anomalies reaching a set threshold can be identified instantly.
AI also allows our cybersecurity solution to learn about the cyberthreat profile faced and adapt accordingly (see Adaptative measure, Adaptive MFA). This capability for quick response and long-term optimization provide a flexible, adaptive, nuanced cybersecurity response that no other IT solution currently can.2.
Importance of behavioral biometrics in AI cybersecurity Traditional cyberprotection tools such as 2FA are often overrated in their effectiveness. Dark web session token can be easily bought for around $10, voiding large parts of the classic 2FA or MFA protocol.
Integrating behavioral biometrics, analysis online behaviour, clicking patterns, mouse patterns, IP location, etc. can add a helpful layer of granularity and earlier detection. Behavioral biometrics also allows us to monitor account usage without interrupting UX of the user (until they should break a higher cyber risk threshold that is configurable).
Conclusion: A brave new world, already around us
Account fraud has become ubiquitous in recent years and shows no sign of abating. We all receive routinely fraudulent SMS or email demanding we “revalidate” credentials, lest the parcel wont be delivered, or the account closed.
This sea change in terms of exposure across society brings profound considerations for application design and security. Gone are the days when users would complain about a 2FA protocol. Users now accept and seek a much higher burden of protection as we have all been exposed to the catastrophic cost of cybersecurity gone awry.
In modern application design, a Smart MFA or the integration fo AI-led behavioral biometrics type cybersecurity may increasingly yield also a net gain in user satisfaction.
Account fraud is also all around us in the existing applications we use.
Large organisations like Google and Microsoft have long integrated some degree of behavioral biometrics in their product UX.
That icon asking you to confirm you are not a robot? The actual clicking matters little, it is more the path of your mouse icon that is considered here to weed out bots.
This approach helps securing applications whilst preserving user experience, making the application monitoring process less intrusive, more adaptive and automated.
Share in
Let’s Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
